Colt Versa SD WAN & SASE – External Service Guide
Contents
1. Overview
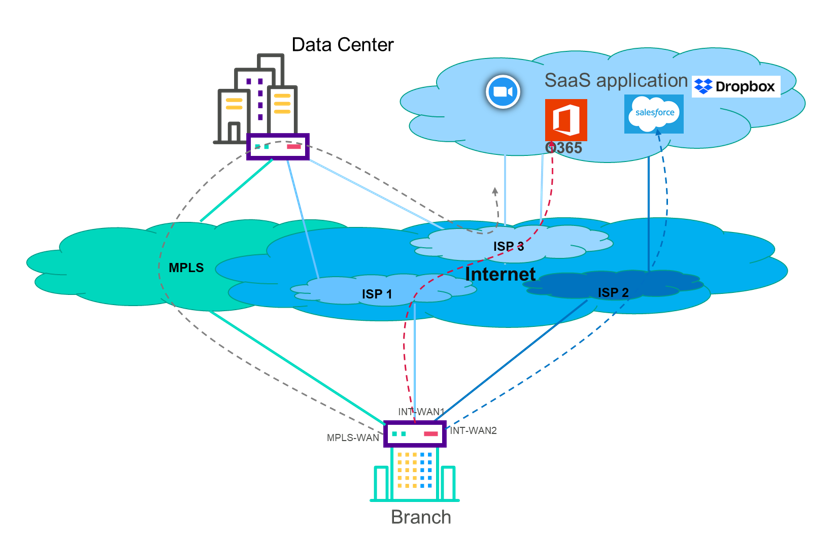
Colt’s Software Defined WAN solution (hereafter SD WAN) enables Internet to be used as a business network and an MPLS alternative for the WAN. There is a radical shift occurring in the market where customers are evolving towards a hyper-connected and digital world by adopting innovative business and operational models (Cloud, Big data, Collaborative tools, etc.). This journey is dramatically changing the requirements for bandwidth, performance, flexibility and agility in the solutions supporting the business and applications traffic.SD WAN gives Customers the ability to combine multiple access connections types (MPLS, Internet, 3G/4G) with application-based policy forwarding and advanced security functions to create a software defined network capable of delivering on changing business needs and capacity challenges.
Colt SD WAN incorporates various software images of Virtual Network Functions (VNFs) deployed on ‘commercially available off-the-shelf hardware components and systems’ for routing, security, WAN and application optimization and analytics. Colt SDWAN makes use of underlay connectivity (private MPLS and public Internet) to establish a secure, encrypted overlay virtual network. Customers can use it to quickly create and deploy a network that offers services like business- grade IP VPN, secure broadband Internet or application-aware routing with full security and QoS over WAN connections. Traffic can be automatically and dynamically (using traffic steering policies) forwarded across the most appropriate WAN path based on network conditions, quality-of-service (QoS) requirements, usage requirements and cost. This combined feature set offers higher network service availability and increased network performance.
In addition, SD WAN allows Customers to optimize the use of their bandwidth through load balancing over multiple Internet uplinks over broadband, 3G/4G (with an Ethernet handoff) in addition to traditional MPLS connections. SD WAN also allows to connect to Cloud service providers and SaaS providers to extend their WAN edge to Cloud.
Colt has upgraded its SD WAN service with the introduction of universal customer premises equipment (uCPE) at the network edge. The service now supports 3pp unmanaged VNF hosting, including CheckPoint Firewall as additional VNFs on uCPE alongside Versa SDWAN VNF. uCPE allows customers to license, manage, and monitor functions with flexible network options, bringing cloud computing benefits from data centres to edge computing at customer premises and branch sites—a new way for enterprises to use connectivity services.
Colt also offers a Wholesale SD WAN solution that offers not only an alternative to an existing vendor, but also the instant ability to a fast time to market when no SD WAN solution is in place for wholesale customer. The Wholesale solution includes Versa SD WAN solution with clear adaptation (customizable portal, branding and further hierarchy levels, systems and processes modification, etc) that allows the Wholesale partner to offer the end-customer an industry leading SD WAN service
The SD-WAN wholesale proposition is perfect for wholesalers without their own solution, seeking a partner to provide a turnkey option with no initial investment or development time. This offering, while limited by resale and vendor restrictions, covers these aspects in detail within the document.
Colt can help to engage this digital enrolment, helping to integrate our existing SD WAN service so that the Wholesale customer can resell it to their end customers, with little visibility about who is actually providing the service in backstage and with full functionality towards them.
There are specific considerations along the processes, that will be covered during the following sections.
2. Benefits
2.1 Available Anywhere
Colt SD WAN service is available to virtually any business address worldwide (basic connectivity pre requisite) in a fully meshed or hub-and-spoke network configuration options.
SD WAN allows connectivity between SD WAN and Non-SDWAN (traditional IPVPN) sites.
2.2 Quick Deployment
New locations can be turned up in as little as minutes with zero touch provisioning (“bringing” the device into the network). Customers will be able to manage their own service, add new branch sites in hours, or upgrade bandwidth in real-time. Colt uses pre-configured CPE devices which are as easy to setup like a home WiFi router.
2.3 Security
Secure end to end connectivity using IPSEC encryption, this ensures that the transit of Customer’s proprietary data is fully protected and inaccessible beyond the intended origination and destination points. Colt SD WAN provides an integrated firewall with SD WAN which provides secure local internet
breakout, provides DDoS protection and ability to create firewall policies and rules through customer portal.
2.4 Connectivity Flexibility
Colt SD WAN services can be provided over public internet – broadband Internet and business internet – dedicated internet access (DIA) connectivity (using any and all transport technologies like xDSL, wireless 3G/4G/LTE (only available in EU for Colt provided SIMs, no limitation for customer-owned), Ethernet or traditional MPLS regardless of whether Colt is providing that underlying connectivity or not. Local breakout is available, if desired, so that only certain traffic is forced through the SD WAN network.
Colt SD WAN supports Colt provided MPLS underlay connection as a standard. MPLS circuit is from Colt or from Colt’s existing MPLS NNI partners. Any new MPLS provider needs an MPLS NNI to be setup first (see connectivity constraints for Carrier’s provided MPLS legs).
2.5 Application Performance
Based on Customer requirements, Colt SD WAN service ensures that it always provides the best available connection for traffic flows based on jitter and latency requirements. In addition, Customers are in complete control of steering traffic over specific preferred links through the use of layers 3, 4 and 7 based
access control lists and policies that can be implemented via the self-service portal.
2.6 Self-Service Portal
The Colt SD WAN portal allows dynamic management of network based on Customer requirements, with policy control and visibility, traffic data reporting is also available for visibility of throughput (peak/average) and traffic volume for a selected duration.
For the Wholesale SD WAN service, both wholesale customers and end customers will benefit from a customized look and feel, setting wholesale customer’s own logo, background image, links and contact details, so that their end-customer experience doesn’t differ from the rest of their services offered.
2.7 Service Reliability
Multiple points of presence, bidirectional metro rings, and a fully redundant network core support ensures service availability and that customer data gets to where it needs to go.
2.8 Redundancy and High Availability
Colt SD WAN service can be deployed in a redundant and highly available manner, supporting link level and device level redundancy to eliminate single point of failures. In addition, the back-end control and provisioning systems are redundant as well to ensure service availability is not affected by any single point of failure.
2.9 Cost Efficiency
Colt SD WAN provides the ability to manage and optimize traffic over multiple infrastructure links and maximize the use of bandwidth thereby lowering costs. Customers can use it to top up existing IP VPN bandwidth by using the Internet in addition to existing IP VPN bandwidth; another use case would be an Internet only version which can be used where dedicated leased line cannot be justified due to cost reasons.
2.10 Control (Changing Traffic Patterns)
SD WAN gives the ability for customers to route their traffic for specific application based on a number of parameters. Traffic policies (MPLS vs internet) will be set during the initial deployment and will be based on basic business rule settings (IP address/subnet, protocol and/or port number, preloaded applications), these can be changed any time via the self-service portal.
2.11 Analytics
Near real time, interactive dashboards that enable Customers to keep view the health of a network and applications by continuously monitor traffic flows and enabling the identification of and response to business impacting events. Visualization of application performance, network security and Firewall, and
utilization – allowing organizations to analyse issues at the site level, application layer, or individual user level.
2.12 Multi-cloud
With With SD WAN Multi-Cloud, customers are able to connect their branch sites directly to all their cloud-based SaaS and IaaS workloads and manage this connectivity centrally via the Colt SD WAN portal. It brings together a single cohesive view of the enterprise network, tying together WAN sites, IaaS/Cloud sites, and traffic towards SaaS cloud – all easily viewed and managed via the Colt SD WAN portal. SD WAN Multi-Cloud extends the SD WAN benefits of security, analytics and optimization to connectivity to the Cloud Service Provider and provides an end-to-end SLA for all connectivity types (MPLS, Internet, Wireless and Cloud) for enterprise networks.
Colt SD WAN Multi-cloud services are available in Europe and Asia and supports direct connectivity towards Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. The SD-WAN Multi-cloud solution uses gateways hosted in the Colt network with dedicated connectivity into the Cloud. Today, Colt is monitoring proactively our Cloud Gateway infrastructure, cloud providers at an application level. Within the direct connectivity program of the CSP, Colt supports both hosted and dedicated CSP options in the likes of AWS Direct Connect, Azure ExpressRoute and Google Cloud Interconnect (GCI).
2.13 Support for IPv6
Internet Protocol version 6, is a new addressing protocol designed to incorporate whole sort of requirement of future internet known to us as Internet version 2. This protocol as its predecessor IPv4, works on Network Layer (Layer-3). IPv6 provides larger addressing space and simplified header. Colt SD
WAN supports use of IPv6 addressing on LAN interface. Colt SD WAN supports use of IPv6 addressing on WAN interface for single CPE, single internet with IPv6 only
2.14 WAN Optimization
SD WAN with WAN optimization provides customer an enhanced user experience as it improves the network performance and reliability over multiple wan links for a site. It alleviates the effects of latency that maximize bandwidth utilization and relieves network congestion. The advantage of SD WAN with
WAN optimization is that it is aware of other network traffic on the same link and can intelligently manage all flows overcoming the problems of TCP retransmission.
We utilize following traffic optimization techniques
- Forward Error Correction (FEC): Allows missing data packets to be recreated at the destination without adding latency or jitter
- Packet Cloning (Replication): Mirrors packets between two or more paths – if one packet is lost, the mirrored packet will still be delivered
3. Service Design
3.1 Transport agnostic Application driven WAN
Colt SD WAN ensures Customer WAN network is designed to provide efficient application performance irrespective of the underlying transport (MPLS or Internet). The service enables and implements application routing policies and also allows for load balancing of default traffic in order to ensure that all
available WAN capacity is optimally utilized.
3.2 Site design types – SD WAN Service Pack (Multiple WAN Links)
Colt SD WAN supports multiple access types to suit individual site requirements; these can include dedicated Ethernet, Direct Internet Access, cost-effective broadband DSL connectivity or 3G/4G/LTE. By default 3G/4G circuits should be used as backup only if fixed Internet and MPLS circuits are available i.e. traffic should not load-share across 3G/4G and other WAN circuits. The SD WAN CPE can be attached directly to the Internet Access circuit (recommended) or behind a customer router or modem device. The handoff to the SD WAN CPE should be plain 802.3 Ethernet (no VLAN tagging) or PPPoE (with or without VLAN tagging). PPPoE handoff (with or without VLAN tagging) has been validated and enabled for France only (with Bouygues Telecom) currently.
Blue Wireless
Colt now offers a Fixed Wireless, 4G/ 5G cellular Internet access service to our customers. This service is a complete resell of the Wireless Internet access service provided by Blue Wireless, a Singapore-based company. Uniform service including on-site survey, installation, maintenance and operation can be provided in about 90 countries in Europe and Asia as well as in North America, South America and the Middle East. This service comes with Cradlepoint mobile router, Dual SIM and its data, installation and operation service, and SLA. This service offers managed mobile internet access service maximum up to 300Mbps/30Mbps(Down/Up) supports both unlimited data and limited data plan with flat rate pricing. This service guarantees 50% of contract speed.
The service can also be utilised for SDWAN customers as an Internet underlay, typically utilised as a backup to existing fixed WAN connections or for low priority site locations where physical connectivity is difficult to achieve.
All countries where Supplier has the network coverage (~ 88 countries) and where Colt is authorized to sell. Not all these plans are available in all locations, for several reasons.
As part of the ‘Partner IP Access’ product, Colt has chosen Blue Wireless to provide an end-to-end managed service supplying Wireless Internet connectivity using 4G LTE/ 5G cellular technology with a managed CPE. The standard service offering delivers a Blue Wireless managed Cradlepoint CPE with dual resilient SIMs as below:
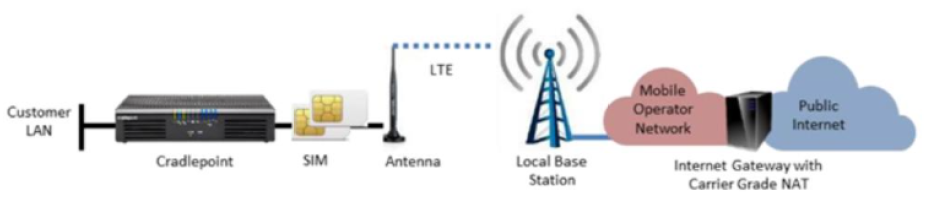
There are 2 service offerings by Blue Wireless, Primary mode and Backup mode. Primary mode has an unlimited data plan expected to be used for most typical enterprise customer use cases and a backup mode offering that comes with a data limit. Typically, 10GB per month and over usage restriction, along with 30GB data Uplift plan for backup mode. Over usage will automatically downrate the access line to a minimal speed (1Mbps/1Mbps), which ensures the service is not completely down when the data limit has been reached but will result in a poor customer experience for normal everyday applications. Low bandwidth applications could still function such as credit card transactions as an example but would be very limited.
Blue Wireless offers a number several bandwidth plans
Not all these plans are available in all locations, for several reasons. Some MNOs are not offering all these plans in all regions. Some (higher) speeds might not be attainable due to the local environment the Cradlepoint CPE will be in. Blue Wireless will test the speed before handing over the service to Colt / customer
The Service offer two data plan options for customer to choose from, to be Indicated in the Order.
- Unlimited Data (Primary Plan), offering unlimited data usage at the contracted Maximum Access speed at a fixed MRC. The Service is configured as an active access for the primary connection.
- Limited Data (Failover Plan), where there is predefined amount of data usage included per month indicated in the rate card to be used at the contracted Maximum Access speed at a fixed MRC.
An option may be provided to increase the predefined amount of data usage per month. Upon reaching the data limit, the maximum access speed will be throttled to 1Mbps/1Mbps speed. The blue wireless CPE can be attached to any of the current standard Versa CPEs – no new colt managed hardware is introduced for Blue Wireless connections
Based on the maximum bandwidth supported by Blue wireless i.e. 300Mbps/30Mbps(Down/Up), following T-Shirt sizes/packages are in scope of current phase:
- XS – Extra small
- S – Small
- S Plus – Small Plus
Key points
- Blue wireless connections shall be ordered as part of IP Access underlay
- Maximum 1 Blue Wireless link per site, both for single or dual CPE setups, is supported
- Internet Egress is only available for unlimited plan
- IPv6 is not supported
- uCPE is not supported
- Blue Wireless (with limited plan) and a 4G connection at the same site is not supported
- Zscaler SSE solution has been technically validated with Blue wireless with Unlimited plan but not the Versa SASE yet.
- Customers shall ensure that the CradlePoint device Installation must be carried out at the location where Versa CPE is expected to be installed in order to achieve a direct connectivity between these two devices. In case Blue Wireless considers that coverage is not good enough and SLAs are at risk, they will evaluate the installation of a 10m indoor external antenna to get the right signal out of the rack. Customers are always advised to increase the default coverage of the CradlePoint equipment by installing it on top of the rack where the SDWAN box is installed. If in case the indoor external antenna does not suffice to guarantee Blue Wireless Service, the CradlePoint equipment will be installed elsewhere in the building where signal is good enough and customer will be responsible to install the required internal cabling considering RJ45 demarcation towards Colt SDWAN equipment. And it is customer’s responsibility that the CradlePoint device must not be shifted from the install location as performed by Blue Wireless.
- As Blue wireless connection is a wireless connection, It should not be considered as one to one replacement of any wired internet access considering different performance matrix like latency. Blue wireless connections latency is expected to be higher then the wired internet connections, especially in case if inter-regional site to site communications.
- Blue Wireless does not offer any guarantees on the Latency, Jitter and Packet Loss but Blue Wireless will endeavour to optimise the performance.
Note: Due to some regulatory limitations, blue Wireless do not offer services in following countries: India, China, Russia, Cuba, Syria, Iran, North Korea, Venezuela
Blue Wireless – Starlink Satelite
Blue Wireless, in partnership with SpaceX, provides Starlink satellite services. Following satellite services are supported as an underlay for the Colt Versa SD WAN solution:
- Global Managed LEO Plus (GML+), based on a combined Satellite and LTE/5G connection using a performance satellite antenna and cellular antenna.
- Global Managed LEO (GML), based on a single Satellite connection using a performance satellite antenna.
These plans are supported as an underlay for the Colt Versa SD WAN with the following guidelines:
- Leo, Leo+ with limited data plan only
- Leo, Leo+ available as backup/secondary connection only
- Only Public IP Supported
- Supported with SD WAN XS, S and S Plus Packages
- Supported with SD WAN CPE Models: v120, v210, v220
- Supported with Following SD WAN site topologies:
| Limited Data Plan | Connection Supported |
|---|---|
| Single CPE LTE Only | Primary LTE or Leo/Leo+ |
| Single CPE Hybrid [LTE] | MPLS + LTE or Leo/Leo+ |
| Single CPE Dual Internet LTE | IPA (wired, not Leo) + LTE or Leo/Leo+ |
| Dual CPE Hybrid LTE | MPLS (wired) + LTE or Leo/Leo+ |
| Dual CPE Dual Internet LTE | IPA (wired, not Leo) + LTE or Leo/Leo+ |
Below is a table summarising the standardised packages that are available for customer to order per site.
Each size package varies in the type and number of WAN uplinks, number of CPEs, bandwidth, diversity, and service assurance.
To build a new SD WAN solution, simply work with customer to mix and match these ‘sizes’ to meet the requirements for each site.
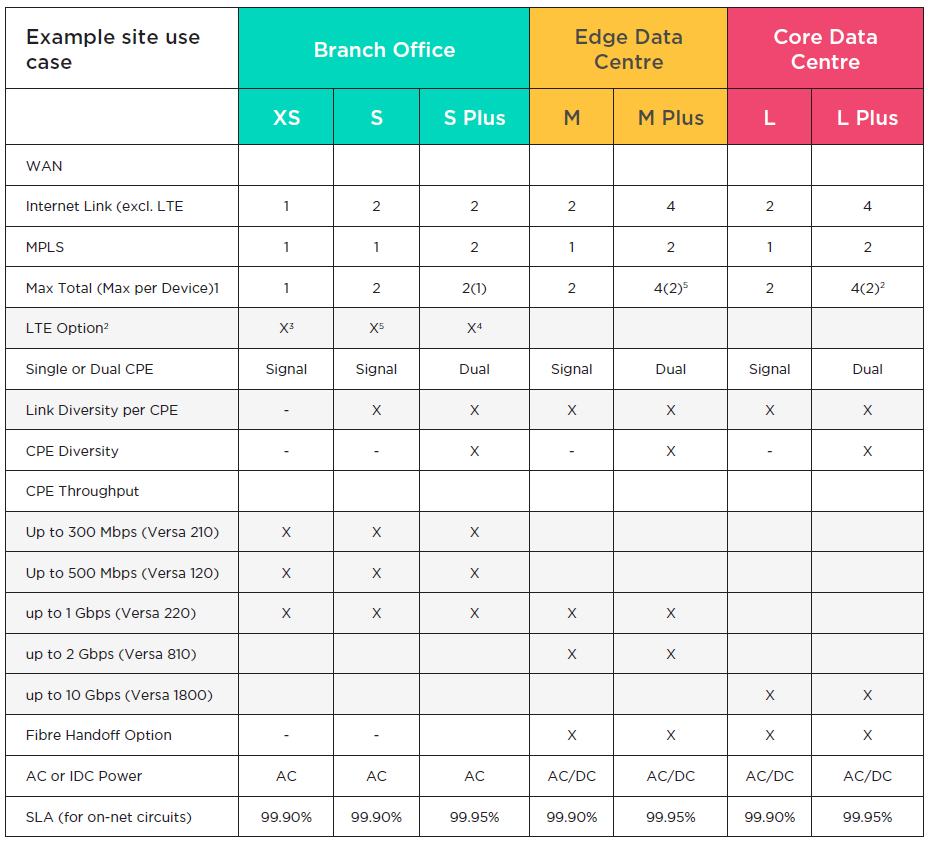
Note: Blue wireless connections are supported for XS, S & S Plus packages only currently.
- Any combination of Internet and MPLS uplinks up to the max supported and not
exceeding maximum for each type. - LTE as substitute or in addition to any fixed Internet connections.
- LTE substitutes the fixed WAN Uplink
- Dual LTE not supported in combination with Fixed MPLS or Internet uplinks. Single
LTE uplink is on primary CPE when combined with 2 fixed uplinks. - Max 1 MPLS per CPE. Single MPLS is always on primary CPE.
- For 2 Internet uplinks LTE substitutes the second Internet uplink
To illustrate these site size packages further, see the example use cases below:
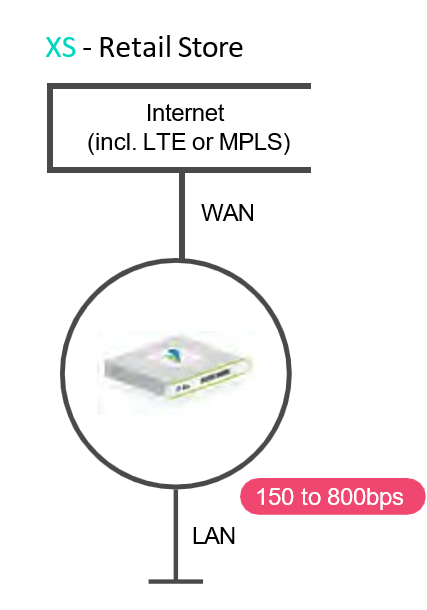
XS package is the entry level connectivity option for customer sites to be connected using a single CPE with a single WAN uplink (either MPLS or Internet, including LTE). There is no redundancy in the solution design, and The CPEs used will be the V120, V210 & V220 BWs from 300Mbps to 1 Gbps
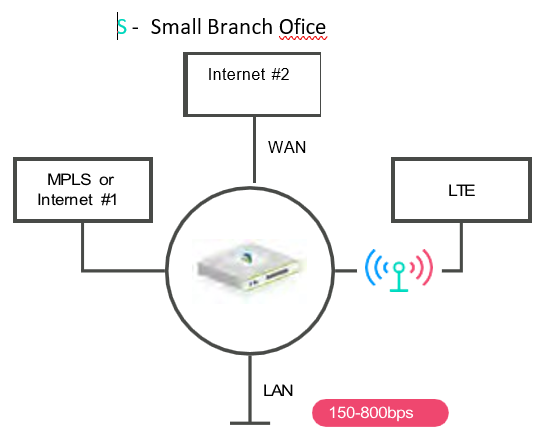
S package provides two WAN uplinks using a single CPE with link diversity. It supports access redundancy with both lines in an active- active configuration, allowing total available bandwidth to be used under normal traffic conditions. It is important to note that both uplinks should have the same nominal bandwidth to optimize the
results of the active-active usage of both access lines and best path routing and traffic selection path. The CPEs used will be the V120, V210 & V220 BWs from 300Mbps to 1Gbps
S plus package is useful for customers requiring a higher resiliency level, providing CPE diversity.
Two CPEs are deployed with back to back connectivity, with a maximum of one WAN uplink per each CPE
The CPEs used will be the V510, V120 & V220 BWs from 150Mbps to 1 Gbps The CPE model used in L package will be the V810, offering a maximum BW of up to 2 Gbps

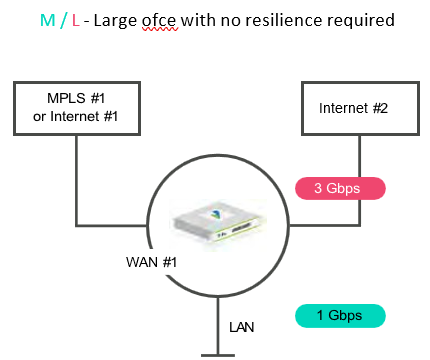
M/L packages are a perfect fit for large office sites that require multiple WAN links but no CPE resiliency.
Both provide a maximum of two WAN uplinks, that can be either two
M / L – Large ofce with no resilience required internet (no LTE) or one internet plus an MPLS leg.
The CPE model used in M package will be the V220, offering a maximum BW of up to 1 Gbps.
The CPE model used in L & L Plus package will be the V1800, offering a maximum BW of up to 10Gbps.
Both support fibre handoff option.
M/L plus packages are a perfect fit for data centre sites that require multiple WAN links but with CPE resiliency as well.
Both provide a maximum of four WAN uplinks (two per CPE), that can be either two internet (no LTE) or one internet plus an MPLS leg per CPE.

The CPE model used in M & M Plus package will be the V220, offering a maximum BW of up to 1 Gbps.
The CPE model used in M & M Plus package will be the V810, offering a maximum BW of up to 2 Gbps.
The CPE model used in M & M Plus package will be the V850, offering a maximum BW of up to 3 Gbps.
The CPE model used in L & L Plus package will be the V1800, offering a maximum BW of up to 10Gbps.
Both support fibre handoff option.
3.3 Traffic flows
The customer may have a mix of sites – IP VPN on-net sites (connected directly to Cisco based MPLS network) or SD WAN hybrid sites (OLO MPLS and Internet lines, Versa based) or SD WAN Internet only (Versa based) or SD WAN MPLS-only site.
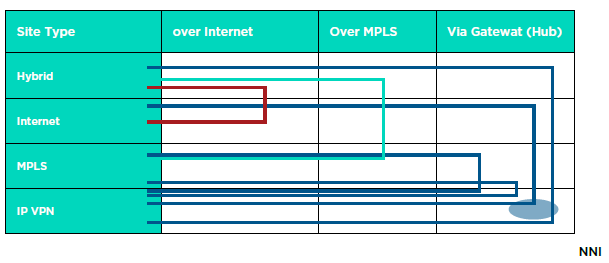
The table below provides the overview of the traffic flows with regards to how SD WAN gateways and Encrypted tunnels are used (Versa uses IPSec but combined with other protocols)
| Site Type | MPLS+ Internet | MPLS Only | Internet Only | IP VPN |
|---|---|---|---|---|
| MPLS + Internet | Encrypted | Encrypted | Encrypted | IPSec till one end of SD WAN Gateway, and then Normal IP VPN on the NNI from Gateway to PE from the other leg |
| MPLS only | Encrypted | Encrypted | Encrypted (via Gateway) | IPSec till one end of SD WAN Gateway, and then Normal IP VPN on the NNI from Gateway to PE from the other leg |
| Internet only | Encrypted | Encrypted (via Gateway) | Encrypted | IPSec till one end of SD WAN Gateway, and then Normal IP VPN on the NNI from Gateway to PE from the other leg |
SD WAN Gateways provide the following functions 1) they act as a transit gateway between the encrypted SD WAN VPN and a normal IP-VPN and 2) They act as a hub for connecting SD WAN sites on disjoint networks e.g. a site connected to MPLS only and a site connected to Internet only. SD WAN Gateways are implemented on a region by region basis to reduce the latency caused by backhauling tunnels
3.4 Application aware connectivity
Colt SD WAN service delivers path control for application-aware routing and forwarding across the WAN. It supports, dynamic selection of the best path for application-based business policies and application-based load balancing across paths for full utilization of bandwidth with improved network availability.
3.5 Encryption
- Encryption method: Advanced Encryption Standard AES-128 and AES-256 supported.
- Authentication Method: Secure Hash Algorithm SHA2.
- Internet Key Exchange (IKE): IKEv2.
- PSK: As standard, pre-shared keys will be used to authenticate between IPSec peers.
(For Colt SD WAN, Colt owns & manages the keys).
4. Features
Colt SD WAN is an evolving product line, this is primarily because the industry is still evolving with ongoing developments (Colt product offering is mature as committed). Colt will continue to improve and add new product features and they will be added in this guide as they are released (please refer to roadmap for details).
4.1 Customer Portal
Colt SD WAN Portal is a self-service portal available for both Carrier and end customer. It enables network services to be used, modified and orchestrated on real-time and on-demand basis – as is typical for cloud services. As it is ‘software defined/controlled’, the WAN transforms into an agile, flexible network enabling a customer to be in control of its network.
In summary, the portal gives the Customer the ability:
- To map applications to specific WAN uplink (eg., MPLS and/or Internet)
- To choose when an application needs to switch to the secondary path
The SD WAN portal is intuitive and easy to navigate with below features:
| Portal Pages | Page Details |
|---|---|
| Dashboard | Gives an overview of all provisioned sites on a geographically accurate map Dashboard allows regularly used graphs or reports to be pinned to the Dashboard view. Status of Pending orders are listed |
| Policy Management | per site traffic steering policy rules per site add, delete, edit and back-up traffic policies map traffic to WAN uplinks on multiple parameters like source and destination IP Address, source and destination port/socket, protocol and applications (more than 2,500 applications supported) define policy to switch between WAN links based on latency, jitter, packet loss, traffic Rx/Tx thresholds Multiple metrics per policy can be added Bulk copy pushes policies to multiple sites by single button click |
| Firewall Management | per site firewall rules overview per site add, delete, edit and back-up firewall policies Policies applied to Internet and SDWAN for both inbound and outbound traffic Create firewall rules based on multiple parameters like source and destination IP Address, source and destination port/socket Create Application layer inbound and outbound Firewall policies with source/destination IP addressing Create DNAT for LAN and DMZ zone rules by IP address and port number Bulk copy pushes policies to multiple sites by single button click default policy deny all |
| Firewall analytics | lists all active firewall rules top 10 (or more) applications with sessions, traffic Tx/Rx and bandwidth used historical view by day, week, month or custom time frame |
| Interface Analytics | delay, jitter, loss ratio, traffic in/out and number of sessions on per interface basis historical view by day, week, month or custom time frame |
| Application Analytics | application bi-directional bandwidth utilization top application information pertaining to sessions, and traffic utilization (Rx/Tx) Application view can be filtered or selected per application historical view by day, week, month or custom time frame |
| DDOS | create DDOS attack profiles and suspend actions historical view by day, week, month or custom time frame of DDOS attack analytics associated with attack profiles. |
| Device | detailed CPE hardware information self CPE diagnostics, including ping and traceroute Data synchronization icon to re-synchronize the Portal and SDWAN bases. WAN interface details including MAC, status, IP address, speed, traffic Rx/Tx and QoS policies LAN interface details including MAC, ARP information, IP address, speed, and routing policies |
4.2 SD WAN wholesale customer portal specifics
Colt SD WAN Portal for the Wholesale segment can have a personalized branding and domain, and therefore there are some requisites the wholesale customer needs to fulfil.
All the required information needs to be captured by Sales teams and shared to Portal team to set up Reseller’s SD WAN portal.
At the same time, special flag within the order form will remind the user that this requirement needs to be taken care of prior to service delivery.
Main requirements:
- Select a domain name for the branded version of the portal (e.g. sdwan. reseller.com)
- Update the Carrier’s own DNS records to associate this domain name with the Colt production portal, either:
- as a CNAME record pointing to sd-wan.colt.net or
- as an A record pointing to the colt-owned IP address: 217.111.165.33
- Obtain an SSL certificate to secure web traffic to this domain.
- The associated private key for this SSL certificate should be a minimum of 2048 bits long.
- The certificate should be signed by a widely trusted Certificate Authority – e.g. Verisign
- The certificate expiry date should be a minimum of 365 days from the date of issue
- Neither the key nor the certificate should be password protected
- Using the following pages as a starting point, collect content that the Carrier wants to be shown on the branded portal.
- Not all content is mandatory (e.g. a login logo), but if it is not supplied, then the corresponding area of the screen will default to blank
- Image sizes and other constraints apply
- Send the certificate, the private key and the branding information to the SDWAN Portal team.
- For testing purposes, a Colt Demo portal can be set up as well with the customized look and feel
- Carrier is responsible for end-customer credentials and password management, that would be created within their user access to the portal (tenant management). End-customer will not be able to manage his credentials, only to ask for a reset to Carrier.
4.2.1 SD WAN wholesale customer portal branding
In order to customize the specific branding for each wholesale customer, Following information essential to be captured from wholesale customer:
- Splash screen background image
- Min 1920px wide, 1440px high, PNG or JPG format
- Login dialog logo
- Max 250px wide, 200px high, PNG or JPG format
- Forgot password link (required)
- URL only (text will be unaltered)
- Footer HTML (required)
- HTML inside a DIV element, maximum 2 lines high. <ul><li> elements will be separated by vertical bars
Once in the SD WAN Network Dashboard, there are some other items that can be customized as well:
- Application logo
- Max 250px wide, 32px high, PNG or JPG
- Help link (required)
- URL only (text will be unaltered)
- NOT SHOWN:
- Web page title (text only)
- FAVICON.ICO icon to show in the address bar (48×48 px or 24×24 px, icon format)

In case the customer doesn’t want to customise the landing page or the SD WAN dashboard logos, Colt can also offer the possibility of not showing any logo instead.
Technical details as registered domain, SSL certificate or even the Help and support & Forgot password links are mandatory.
API integration with SDWAN Portal is possible but not as a standard switch on/off capability. API integration with SDWAN portal will require some efforts to understand customer requirements and development. Based on the initial analysis, SDWAN portal integration cost could be provided.
Note: Pease refer to Portal Guide document for further details
4.3 Dynamic traffic steering
Dynamic multi-path traffic steering is a real-time portal driven feature that helps Customers utilize both MPLS and Internet uplinks in a redundant or load sharing configuration. In addition to detecting pre-configured applications, traffic can be routed through IP address, protocol and/or port (socket) numbers.
Customers can choose to do (add/edit/ delete) all their policy configurations anytime via the secure Colt SD WAN portal.
Colt SD WAN platform measures jitter, packet-loss, round-trip delay, traffic utilization TX/RX in all the paths between branches or between branch-to-hub. Please see portal appendix for policy configuration details.
4.4 Optimum path selection
Optimum Path Selection is a default SD WAN portal feature for all customers that provides the best path selection between all possible paths when a 10 % variance of performance is reached. The standard SDWAN traffic Steering rules through SD WAN portal provides path selection based on circuit priorities and/or SLA thresholds instead of performance. Optimum path selection can steer traffic based on one or combination of several metrics, For example lowest latency, lowest packet loss or lowest delay variation. Besides traffic selection, our existing SD WAN traffic steering options remain available.
These include:
- Configuration of different circuit priorities
- Configuration of SLA thresholds for several metrics: Latency (ms), Jitter (ms), Packet loss (%), Transmit/Receive Bandwidth utilization (%)
- Continuous evaluation of the traffic sessions that provides the traffic switching between difference paths, when the used path is no longer SLA compliant or there is a better option with <10% of difference
4.5 Analytics
Supported for interface, firewall and applications. These are on near real-time basis with based on logs sent from branch sites and stored in the analytics database . Historical views are also supported along with deeper granularity. Please see portal appendix for details.
4.6 Routing between Colt managed CPE and customer LAN
Both static and dynamic routing supported. Static, BGPv4 and OSPFv2 routes are all supported on SD WAN CPE for routing towards the customer LAN.
4.7 DHCP
DHCP requests from local clients are forwarded to Customer owned/managed central DHCP server (applies for IP addressing on the Customer LAN, not static or DHCP config in the WAN if customer is providing own Internet). Colt SD WAN CPE adds its own information to the request to identify the site (to enable the central server to allocate address from appropriate pool). DHCP server can be delivered as a bespoke on customer special request.
4.8 IP address management
Customer IP addresses may be private or public as the service treats the addresses relevant only to the particular customer VPN.
As per DHCP, it applies for IP addressing on the Customer LAN, it does not refers to the WAN if customer is providing own Internet.
- IPv4 & IPv6 are supported
- By default static routes shall be used for all the addresses for each site. As an option, routing protocols may be enabled as well at the time of ordering the service.
4.9 Local internet breakout
The Local Internet breakout feature allows ‘to/from’ internet traffic to utilize an SD WAN site’s local internet connection rather than going through the central network gateway. Any traffic other than which is destined for SD WAN sites (e.g. to access legacy applications residing at an enterprise location) will access the internet using the local internet connection.
A key benefit of local breakout is the user experience when accessing trusted applications as these can be accessed locally and hence avoids unnecessary latency. In addition local breakout helps reduce the customer’s bandwidth needs across Colt SD WAN platform.
By default a Deny-All rule is applied for traffic between the LAN and Internet in both directions. The customer can then add rules to selectively allow traffic towards and from the Internet e.g for trusted applications such as Office 365.
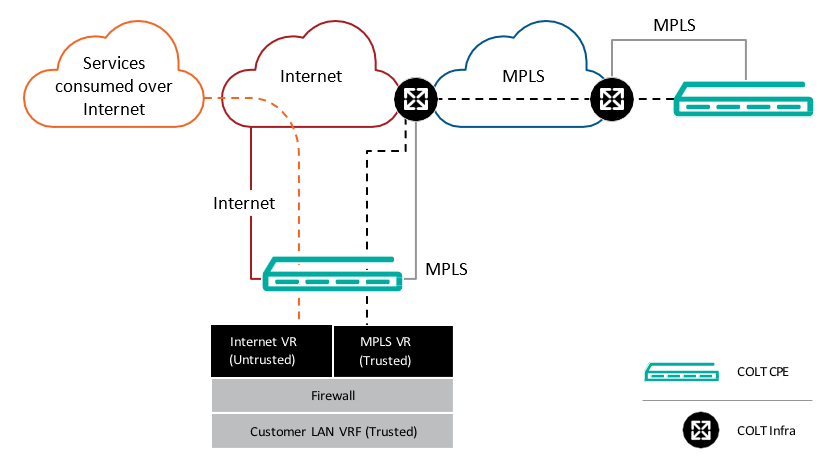
Local Internet breakout is a default Colt SD WAN service feature, if an Customer, for any specific reasons, wants central internet breakout (central gateway) then it will be handled as a bespoke request and would need a modification order.
Highlights:
- Default option
- Will be on the first internet connection (more than one internet connections possible)
- Available on all site types that have an internet connection
- With dual internet, the local internet breakout will be on an active/standby basis (could be load balancing if requested by customer)
- With dual CPE, internet breakout will only be on the internet attached CPE
- With MPLS/internet, breakout will only be available on internet connection at that site
Multiple Internet – LIB
A local internet breakout is an access point to the internet located as close to the user as possible. Local breakouts enable organizations to offload internet-bound traffic from local branches and remote offices, and route it directly to the internet via a local internet service provider (ISP).
- Customers will be able to select the Internet links and resiliency mode (load-sharing or active/standby) through SDWAN Portal.
Our solution Multiple LIB customers can benefit from the below,
- With the introduction of multiple WAN Uplinks, the customer can have up to 4 Internet uplinks.
- Through SD WAN portal customers can select the Internet links and resiliency mode (load-sharing or active/standby)
- By default, for all sites enabled for LIB in order system will have the internet wired uplink enabled in Active/Active mode.
- The Customer will have the option to change the default mode to Active/Standby based on the defined priority of Internet links via portal.
- Customers can now selectively enable or disable specific Internet links for Internet access from SDWAN portal.
LIB can be configured in two modes as per below picture.
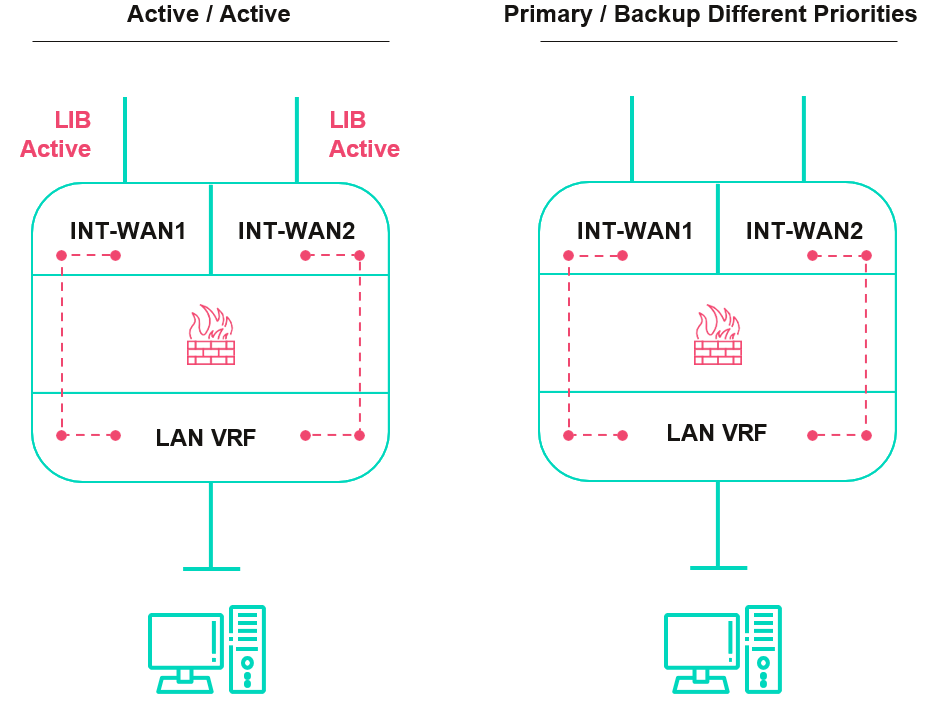
4.10 Standard firewall
Colt SD WAN platform comes equipped with an L4 Stateful firewall (Versa FlexVNF Stateful FW feature on CPE). It supports rules around source and destination IP addresses, source and destination port and/or protocol numbers. When a customer site is first activated, the default firewall policy is to allow all traffic between SD WAN sites and “deny all” in both directions between the customer LAN and Internet. As an additional option, SD WAN firewall can be enabled which extends the default “deny all rule” to traffic between SD WAN sites. Firewall policy rules can be modified using the SD WAN portal.
Firewall rules are standard and based on simple allow, deny or reject commands on any of the defined parameters. Rule can be applied to a single or multiple CPEs.
The firewall feature is integrated with the Colt SD WAN solution and makes use of the stateful firewall feature embedded in the Versa FlexVNF software. This avoids the need for a separate firewall solution.
Highlights:
- Control – add, delete, modify and prioritize rules
- Back up – switch to any previous (saved) configuration version
- Analytics – there will be user friendly graphical analytics allowing users to view the number of allow and deny logs per rule.
Please refer portal guide here for details.
4.11 Advanced firewall
The Colt SD WAN Advanced Firewall feature set is ideal for Customers needing protection against modern web-based security threats like malware attacks, targeted attacks, application-layer attacks; these attacks exploit weaknesses in applications, rather than weaknesses in networking components and services which are the targets of traditional attacks and can be prevented by a stateful firewalls.
The Colt SD WAN platform uses an integrated Next Generation firewall that offers advanced firewall capabilities integrated with the SDWAN router, the functionality can be configured via the Colt SDWAN portal. The Advanced Firewall allows customers to connect separate LAN and DMZ networks to the SD WAN CPE and is used in combination with the local Internet breakout feature.
Colt also offers the Denial of Service (DoS) protection feature with Versa SDWAN. It is used to protect services on the customer LAN or DMZ that are exposed to the Internet e.g. web servers, mail servers. It is only supported in combination with the DMZ / destination NAT feature for the traffic from the Internet towards the LAN/DMZ.
4.12 Dual CPE (High Availability Site)
To enhance resiliency, two SD WAN CPEs are provided in high availability mode, using VRRP to ensure traffic will be routed to the other if either SD WAN CPE fails. By default, not all traffic is rerouted; there may be application exception policies in place for specific applications to avoid Internet or MPLS networks. The dual CPEs form a high availability site with shared aggregated total site throughput.
Dual CPEs can be situated in the same location or different locations, but they require an additional interconnect besides being connected via LAN for VRRP. This additional interconnect is necessary for proper WAN routing.
For the back to back connectivity between the two SD WAN CPEs, the customer can decide whether they need an electrical or optical port
In standard delivery internal cabling can include up to 5 metres, above that needs to be quoted in a case by case scenario.
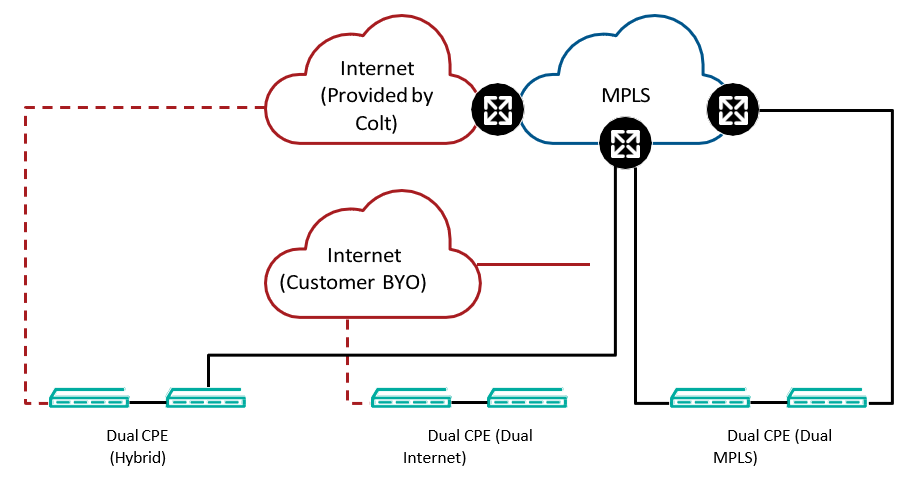
Dual CPE is available in three combinations:
- Dual CPE (Hybrid): Primary CPE with MPLS + Secondary CPE with Internet
- Dual CPE (Dual Internet): Primary CPE with Internet + Secondary CPE with Internet
- Dual CPE (Dual MPLS): Primary CPE with MPLS+ Secondary CPE with MPLS
4.13 CPEs
Versa FlexVNF can be deployed on either a Colt uCPE (not available yet for Wholesale customers) or a Versa Certified Whitebox appliance (Baremetal), both installedon the customer premise. The following appliance types are used based on bandwidth and feature requirements:
Versa – Certified Whitebox Appliances
| Model | Description | Throughput | Uplink | Deployment |
|---|---|---|---|---|
| Versa 510 (EoS) | Advantech FWA- 2320 Intel Atom C2558, 4 core, 8GB RAM | Up to 150Mbps | GbE (Cu) | Small Branch |
| Versa 120 LTE only | EAdvantech FWA- 1010, Intel Atom C2758, 8 Core, 16GB RAM | Up to 500Mbps | GbE (Cu/ SFP) + LTE | Small Branch (with LTE) |
| Versa 210 | Advantech FWA-1012VC-4C, Intel Atom C3000, 4 Core, 8GB RAM | Up to 300Mbps | GbE (Cu/ SFP) | Small Branch |
| Versa 220 | Advantech FWA1012VC. FWA-1012VC- 8CA1V (Versa 220 without LTE) FWA-1012VC- 8CA1VR (Versa 220 with LTE modem for EMEA) WA1012VC2006-T (Versa 220 with LTE modem for APAC) | Up to 1Gbps | GbE (Cu/ SFP) + LTE | Small Branch (with LTE) |
| Versa 810 | Advantech FWA- 3260, Intel Xeon D-1548, 8 core, 64GB RAM | Up to 2Gbps | GbE (Cu/ SFP) | Medium Branch |
| Versa 850 | Advantech FWA-5070L2205-T, Intel(R) Xeon(R) Silver 4210R, 10 core, 64GB RAM | Up to 3Gbps | GbE Cu 10G Fibre | Medium Branch |
| Versa 1800* | Advantech FWA- 5070 Intel Xeon Gold 6212U, 24Core, 96GB RAM | Up to 10Gbps | 10GbE (SFP+) | Hub / Data Centre |
Mentioned throughput are the highest throughput achievable under favourable circumstances. It is the throughput ceiling. The actual throughput & CPE Performance will degrade depending on network and security policies/features applied. CPE performance can be down to 30% on certain CPEs.
Versa 510

Versa 510 Specifications
| Vendor Model | Advantech FWA-2320-01E |
| Processor | Intel C2558 4 Core CPU |
| Memory | 4GB |
| Disk | 64 GB SSD |
| Interfaces | 4 x GbE Cu (WAN/LAN), 2 x GbE Cu Mgmt |
| Power | 100W AC internal PSU |
| Cooling | 1 x smart FAN maximum 37.5dB(A). Front to Back air- flow |
| Physical Format | 1RU rackmount device |
| Dimensions | 426 x 44 x 318mm |
| Weight | 4.5Kg |
Versa 120

Versa 120 Specifications
| Vendor Model | Advantech FWA1010VC. Versa Builds: Versa V120-NW-EX (non LTE) Versa V120-EX-L455-W178 (LTE US/EMEA) Versa V120-EX-L7430-W178 (LTE APAC) |
| Processor | Intel Atom C2758 (8 core), 2.4 Ghz |
| Memory | 16GB |
| Disk | 128 GB SSD |
| Interfaces | 2xGbE Cu/SFP WAN ports, 4x switched GbE Cu LAN ports, 1x GbE Cu as DMZ port |
| LTE/WiFi | WWAN module (Sierra MC7455, MC7430) with antennas WLAN module (Advantech/EWM-W162M) with antenna (not used) |
| TPM | TPM1.2 Module |
| Power | 12V 5A, 60W external adaptor |
| Cooling | 1 x smart FAN with maximum 37.5dB(A). Side-to-side air flow |
| Physical Format | Tabletop device (optional rackmount kit FWA-1010VC- RMT) |
| Dimensions | 250 x 44 x 190.4 mm |
| Weight | 2.3 Kg |
Versa 120 – LTE Modem Specification
| Modem Name | AMER, EMEA: Sierra Wireless MC7455 APAC: Sierra Wireless MC7430 |
| Performance | Cat-6 (peak down-link: 200 Mbps, up-link: 50 Mbps) |
| Wireless Standards | 4G-LTE, 3G (WCDMA) Frequency Bands: MC7455: B1, B2, B3, B4, B5, B8 Frequency Bands: MC7430: B1, B5, B6, B8, B9, B19 |
| FRU | No |
| Geo-Location | GPS, Glonass, Beidou, Galileo |
| SIM Card Access | Externally accessible |
| Antenna | External Antennas that attach to the device are included. Antenna extension (wall mount/roofmount) is also possible. The antenna must have dual SMA male connectors and max 5dbm insertion loss. Example parts include Poynting 4G-XPOL-A0001 (Omni-directional) and 4G-XPOL-A0002 (Directional) |
Versa 220

Versa 220 – LTE Modem Specification
Vendor Model | Advantech FWA1012VC. Versa Builds: FWA-1012VC-8CA1V (Versa 220 without LTE) FWA-1012VC-8CA1VR (Versa 220 with LTE modem for EMEA) FWA1012VC2006-T (Versa 220 with LTE modem for APAC) |
| Processor | Intel Atom C3758 (8 core), 2.2 Ghz |
| Memory | 16GB |
| Disk | 128 GB SSD |
| Interfaces | 4x copper GbE via Marvell 88E1543, 2xSFP & 2x copper GbE via I350 |
| LTE | Sierra/EM7455(EMEA) / MC7430 (APAC) Advanced-LTE module(Cat.6) with related antenna , SMA, screws |
| TPM | TPM1.2 Module |
| Power | 12V 5A, 60W external adaptor |
| Cooling | 2x system FAN with smart FAN |
| Physical Format | Tabletop device (optional rackmount kit FWA-1012VC- RMK) |
| Dimensions | 250 x 44 x 193.04 mm (9.8” x 1.7” x 7.5”) |
| Weight | 2.4 Kg |
Versa 810

Versa 810 Specifications
| Vendor Model | Advantech FWA-3260 |
| Processor | Intel Xeon D-1548(8 core), 2 GHz |
| Memory | 64GB |
| Disk | 256 GB SSD |
| Interfaces | 6 x 1GbE, 2 x 10GbE SFP+, Optional expansion module NMC-1004-10E with 2 x 10G SFP+ with Intel 82599ESx |
| LTE/WiFi | N/A |
| TPM | TPM1.2 Module |
| Power | Redundant 1+Dummy 300W AC PSU. Optional DC PSU |
| Cooling | 4x system FAN with smart FAN. Front-to-back airflow |
| Physical Format | 1 RU Rackmount Device |
| Dimensions | 430 x 44.2 x 500 mm |
| Weight | 15 Kg |
Versa 1800

Versa 1800 Specifications
| Vendor Model | Advantech FWA-5070 |
| Processor | Intel Xeon Gold 6212U, 24C, 2.4GHz |
| Memory | 96GB |
| Disk | 2 x 512GB SSD |
| Interfaces | 9 x 1GbE, 8x10GbE SFP+, Optional expansion module NMC-1004-10E with 2 x 10G SFP+ with Intel 82599ESx |
| LTE/WiFi | N/A |
| TPM | TPM1.2 Module |
| Power | Redund 650W AC PSU |
| Cooling | 3x smart FAN. Front-to-back air flow |
| Physical Format | 1 RU Rackmount Device |
| Dimensions | 41 RU (438 x 44 x 550 mm) (W x H x D) |
| Weight | 20 Kg |
4.14 Universal CPE (only for Enterprise segment)
FlexVNF can also be deployed on the ADVA Ensemble Connector OS and certified uCPE appliances. See the Universal CPE solution guide for further details
Colt uCPE consists of following components
| Component | Details |
|---|---|
| Hardware | Advantech FWA-3260 Advantech FWA-2012 |
| Virtualization Layer | ADVA Ensemble Cloud Suite |
| VNF | Versa SD WAN Checkpoint Unmanaged Firewall |
4.15 Multi-VPN (Multi-VRF)
Multi-VPN feature allows a single SD WAN CPE to be used to deliver up to 9 sub-VPNs (10th is used for uCPE inbound management). On the LAN side, either a separate physical interface or 802.1q logical sub-interface is configured per service instance, and it is placed in the corresponding VRF. On the WAN interface, it’s segregated using VPNv4 addresses. Unlike traditional MPLS VPN- based solutions, multi-VPN does NOT require separate logical circuits on the WAN for each sub-VPN. The SD WAN overlay provides the separation between each VPN
4.16 SNMP RO
SNMP Read-only access allows the customer to poll the MIBS on the Colt SD WAN CPE device from their own network management server. The customer server can be located on the local LAN or on another SD WAN site. SNMPv3 is supported using SHA/MD5 and AES ciphers for authentication and privacy. The type of encryption (privacy) can be: DES/3DES, or AES128
Customers who would like to use this feature need to provide authentication details like: username used in the SNMP requests, authentication password, privacy password. SNMP Traps are not provided by the CPE to the LAN, they are provided from SD WAN controller.
4.17 Advanced traffic steering (application based traffic steering)
Traffic Steering allows application traffic to be intelligently forwarded across different paths between SD WAN sites e.g. Internet or MPLS. By default traffic is load-shared across available paths or the customer can define application based policy. Capability to create traffic steering/forwarding policies based on 3000+ pre-defined applications pre-loaded on on-premise SD WAN CPE.
4.18 Advanced analytics (Versa Analytics) (only available for Enterprise segment)
Advanced analytics for applications by sessions, bandwidth, and access circuit on each branch, including bandwidth consumed by each application. It is accessible through Colt Online, and therefore limited for Colt’s direct customer, not Carrier’s end-customer. Please see appendix for details.
4.19 Self-Install CPE (Zero Touch Provisioning)
A simplified way for Customers to enable Colt SD WAN service globally without having to have technical resources on site. As part of this service, a CPE with basic configuration is shipped to end site where any site personnel (even non-technical) can connect it to the network and complete activation to start consuming the services.
Simple workflow:
- CPE received on site
- Connected to the Internet (to access Colt SD WAN Controller)
- On-site personnel connects a PC to the CPE and accesses a URL provided by Colt
- Colt SD WAN Controller checks the serial number against the URL and if there is a match the post staged customer configuration is downloaded to the CPE and it is launched and connected to Customer subscribed Colt SD WAN service.
Once the connectivity service has been confirmed (whether provided by Colt or the customer), the customer will receive shipment info email with following details.
- Site address details to which the CPE will be sent
- List of requirements for the service to be set-up (e.g. connectivity type, Ethernet interfaces etc.)
- Shipment content (e.g. 10/100 Mbps Managed Optical Demarcation Compact CPE Device, TP-TX/FX-SM1310/PLUS-ST, w/ AC Adapter, Quick Start Guide)
In case of failed self-installation, customer can request the services of an on- site technician. Customers shall incur a service charge at the professional installation rate if the technician determines the failure is directly related to customer equipment, inability or unwillingness to complete the self-installation process or mistakes customer made during the self-installation process.
4.20 SD WAN Multi-Cloud
For customers looking for cost-effective, direct connectivity into multiple cloud environments, SD WAN Multi-Cloud is the optimal solution. It offers private MPLS and/or Layer 3 connectivity into multiple cloud providers in a single solution, combined with end-to-end performance backed by a SLA, end-to- end security, and end-to-end analytics. Colt advises customers to establish resilient connects into their preferred CSP by default, in order to create high Cloud connectivity performance towards the SD-WAN locations. With the SD WAN Multi-Cloud solution, customers are able to combine management of their SaaS/IaaS cloud, WAN, and branch site connectivity into a single intelligent platform. SD WAN Multi-Cloud provides high performance, inexpensive, and secure cloud connectivity directly into the Cloud Service Providers (CSPs)
– Amazon AWS, Microsoft Azure, and Google Cloud.
SD WAN Multi-Cloud provides the following benefits:
Direct and secure Branch to Multi-Cloud connectivity and common policy management
Most companies with connectivity to the cloud are working, not just with a sin- gle cloud, but with multiple cloud service providers. There is a growing need for a simple, straightforward way to manage multi-cloud infrastructures. With SD WAN Multi-Cloud, customers are able to connect their branch sites directly to all their cloud-based SaaS and IaaS and manage this connectivity centrally via the Colt SD WAN portal.
SD WAN Multi-Cloud also offers the ability for customers to manage common policies across their branch sites, SD WAN fabric and multi-cloud environment – further increasing the ease of control over their network.
SD WAN-powered dynamic path selection with SLA
With SD WAN Multi-Cloud, cloud-based applications are intelligently and dy- namically routed to the best available path – minimising risk of performance disruption caused by unpredictable cloud traffic and resulting in an overall improved end-user experience and increased productivity.
Performance visibility across WAN and Cloud, powered by SD WAN analytics
Customers are in full control of their network with Colt SD WAN Multi-Cloud, which provides comprehensive visibility of network performance across both WAN and Cloud. Having this visibility enables customers to monitor, trouble- shoot, and make decisions to improve performance across their network.
Support of Cloud-to-Cloud communication
In many cases, customers’ data will travel through multiple cloud environments. Rather than sending that traffic from branch site to one CSP and backhauling to a data centre or SD WAN gateway to reach another, traffic is routed over ded- icated tunnels from one CSP’s environment to the other. This means reduced latency and optimised performance for the end-user.
Security (Firewall/NAT) between Public and Private Cloud domains
Security remains a top concern for enterprises, particularly in adopting new technologies like Multi-Cloud. With the security features available with SD WAN Multi-Cloud – including Firewalls and NAT (Network Address Translation) – customers can be assured that customer network is secured from the cloud public domain.
With SD WAN Multi-cloud, we can support multiple connections towards differ- ent or same CSP’s using Colt’s Cloud Gateway infrastructure. These connections are always configured as active-active individual connections.
4.20.1 SD WAN Services into Amazon (Amazon Web Services)
Connectivity to Amazon Web Services can be added towards the SD WAN network. Connectivity to AWS can be added to an existing SD WAN network or ordered as part of a new SD WAN deployment. Colt advises customers to establish resilient connects into AWS by default, to create high Cloud connectivity performance towards the SD-WAN locations.
In both cases, connectivity towards AWS from/to the SD WAN network goes via a Cloud Gateway in the Colt IQ Network
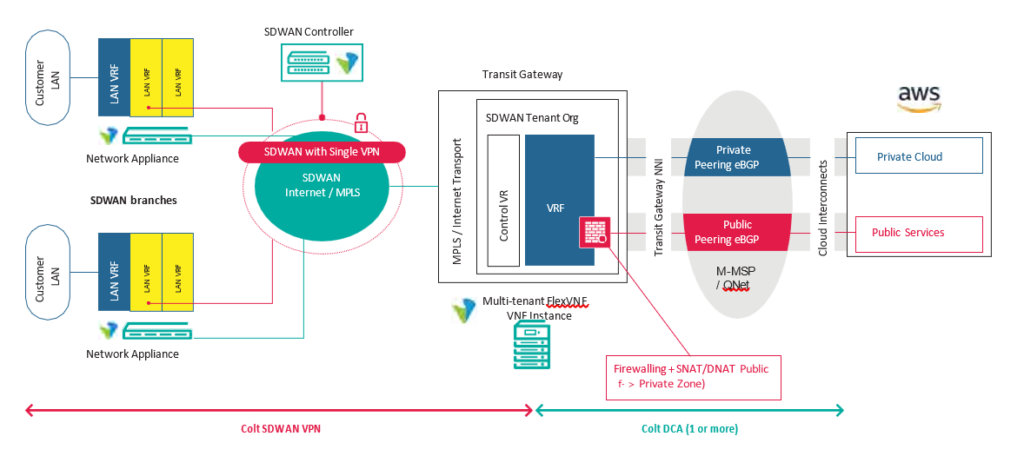
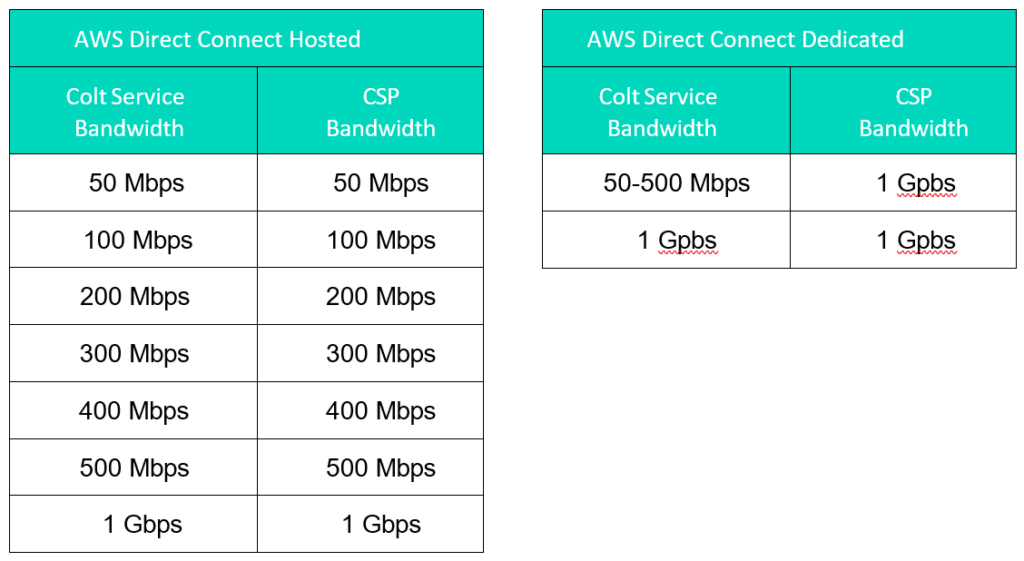
Colt support both the ‘hosted’ AWS Direct Connect option and the ‘dedicated’ AWS Direct Connect port option into Amazon.
For hosted connections customers can choose bandwidth from 50Mbps- 500Mbps in all hosted locations. For dedicated connections bandwidth from 50Mbps up to 1Gbps are supported, please find an overview below:
The existing maximum capacity per Cloud Gateway per customer is 2Gbps. Bandwidths >2Gbps can be supported by distributing connections across 2 or more Cloud Gateways.
The Cloud Gateway supports features like NAT and firewall (for enhanced security).
SD WAN solution into AWS by default supports Cloud-to-Cloud communications between different CSPs, which means that traffic between CSPs does not have to enter the SD WAN network which reduces latency. Customers can order connectivity to any AWS location/region, connected by Colt.
Colt has deployed multiple Cloud Gateways in Europe and Asia to enable resilient connectivity into AWS. To ensure optimal performance of cloud connectivity services on the SD-WAN, customers are requested to order resilient services for AWS.
Colt is a direct partner of AWS and is able to interconnect towards multiple AWS Cloud on-Ramps locations within a metro or cloud region. To offer best performance, Colt routes the Cloud traffic through diverse Cloud Gateways in the Colt IQ Network. Each AWS peering is configured via the AWS Console to support one of the following AWS Virtual Interface types: Private VIF, Public VIF or Transit VIF. For SD-WAN Transit VIF is considered as a Private VIF. Transit VIFs require a bandwidth of 1Gbps and are supported both on AWS Direct Connect Hosted and AWS Direct Connect Dedicated connections. Transit VIFs are available across the majority of Colt’s Direct Connect PoP locations in Europe, Asia and US. Customers are advised to check availability of 1Gbps hosted connections for the required AWS PoP location.
4.20.2 SD WAN Services into Microsoft Azure (ExpressRoute)
Connectivity to Microsoft Azure ExpressRoute services can be added towards the SD WAN network. Connectivity to Microsoft Azure can be added to an existing SD WAN network or ordered as part of a new SD WAN deployment. Colt advises customers to establish resilient connections into Microsoft by default, to create high Cloud connectivity performance towards the SD-WAN locations.
In both cases, connectivity towards Microsoft Azure from/to the SD WAN network goes via a Cloud Gateway in the Colt IQ Network. Note that Colt delivers 2 circuits by default into the Microsoft PoP (each circuit on different Microsoft interconnects).
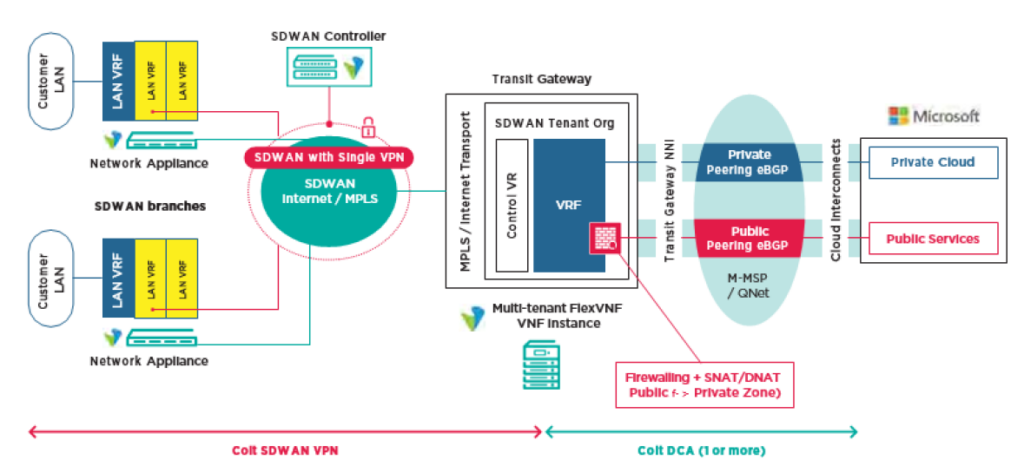
Colt support ‘hosted’ Microsoft Azure ExpressRoute into Microsoft. It supports both connectivity to the “private” Microsoft domain and “Microsoft/public” domain of Microsoft.
For hosted connections customers can choose bandwidth from 50Mbps – 1Gbps, please find an overview below:
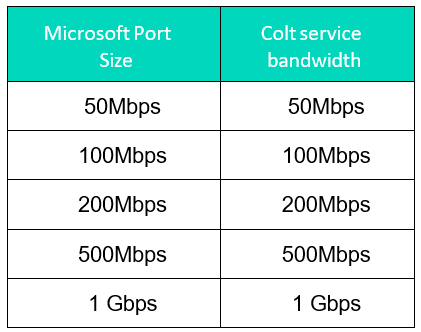
The existing maximum capacity per Cloud Gateway per customer is 2Gbps. Bandwidths >2Gbps can be supported by distributing connections across 2 or more Cloud Gateways.
The Cloud Gateway supports features like NAT and firewall (for enhanced security).
SD WAN solution into Microsoft Azure by default supports Cloud-to-Cloud communications between different CSPs, which means that traffic between CSPs does not have to enter the SD WAN network which reduces latency. Customers can order connectivity to any Microsoft location/region, connected by Colt.
Colt has deployed multiple Cloud Gateways in Europe and Asia to support resilient connectivity into Microsoft. To provide high performance of Cloud connectivity services on the SD-WAN the customer is asked to order resilient service towards Microsoft.
Colt is a direct partner of Microsoft and is able to interconnect towards multiple Microsoft Cloud on-Ramps locations within a metro or cloud region. To offer best performance, Colt routes the Cloud traffic through diverse Cloud Gateways in the Colt IQ Network.
4.20.3 SD WAN Services into Google Cloud Interconnect (GCI)
Connectivity to Google Cloud Interconnect Services can be added towards the SD WAN network. Connectivity to Google Cloud Interconnect can be added to an existing SD WAN network or ordered as part of a new SD WAN deployment. Colt advises customers to establish resilient connects into Google by default to create high Cloud connectivity performance towards the SD-WAN locations.
In both cases, connectivity towards Google Cloud Interconnect from/to the SD WAN network goes via a Cloud Gateway in the Colt IQ network.
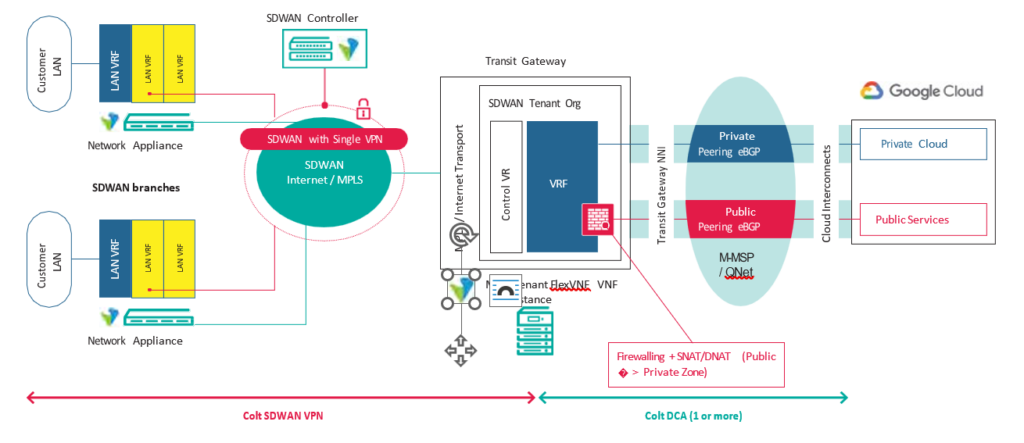
Colt support the ‘GCI partner / hosted’ Google Cloud Interconnect option into Google Cloud. It supports connectivity to the “private” Google Cloud domain.
For hosted connections customers can choose bandwidth from 50Mbps – 1Gbps, please find an overview below:
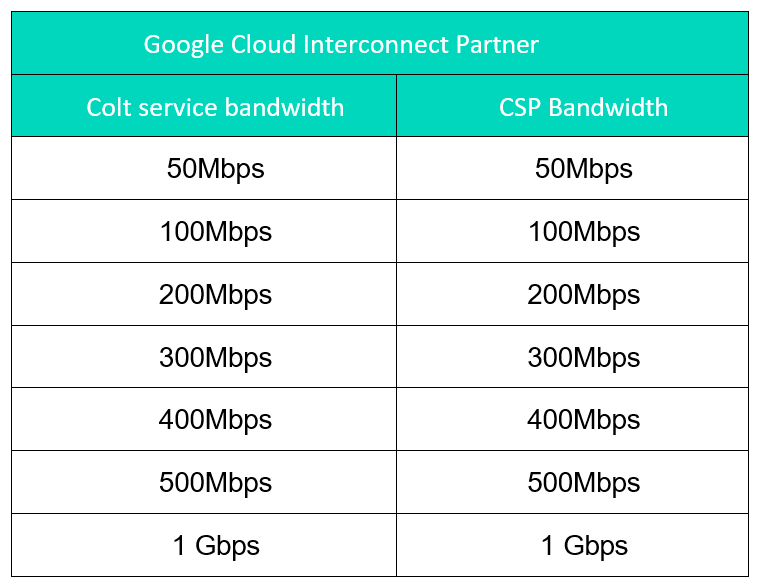
The existing maximum capacity per Cloud Gateway per customer is 2Gbps. Bandwidths >2Gbps can be supported by distributing connections across 2 or more Cloud Gateways.
The SD WAN solution into Google by default supports Cloud-to-Cloud communications between different CSPs, which means that traffic between CSPs does not have to enter the SD WAN network which reduces latency. Customers can order connectivity to any Google location/region, connected by Colt.
Colt has deployed multiple Cloud Gateways in Europe and Asia in order to support resilient connectivity into Google. To provide high performance of Cloud connectivity services on the SD-WAN the customer is asked to order resilient service towards Google.
Colt is a direct partner of Google and can connect to multiple Google Cloud on-Ramps locations within a metro or cloud region. To offer best performance, Colt routes the Cloud traffic through diverse Cloud Gateways in the Colt IQ Network.
4.21 IPv6 support on LAN
IPv6 is supported on LAN-to-LAN communication for the customer (note that Internet Breakout for IPv6 is not supported).
Customers are allowed to provide their IPv6 address and gateway address to Colt, similar to IPv4.
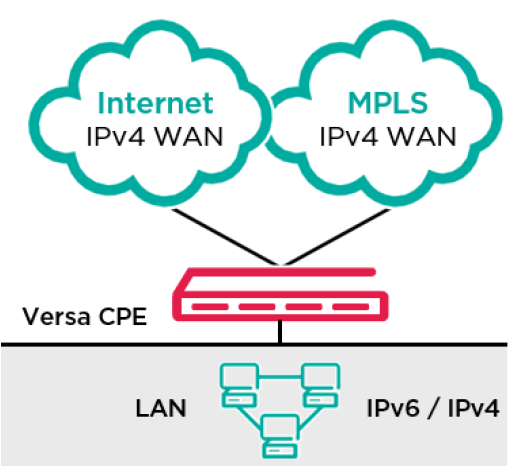
- LAN IPv6 Static Routing
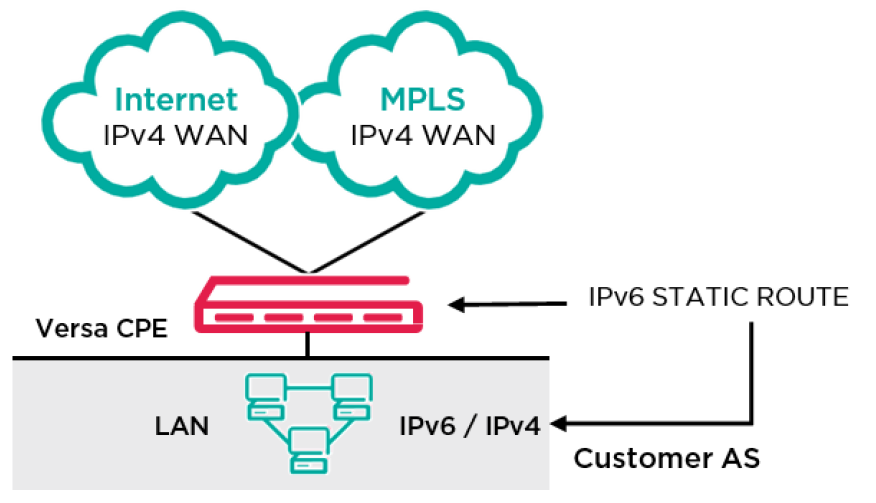
IPv6 route shall be added along with tag numbering using Versa director keeping the next-hop as IPv6 address according to customer’s requirement.
- LAN IPv6 Dynamic Routing
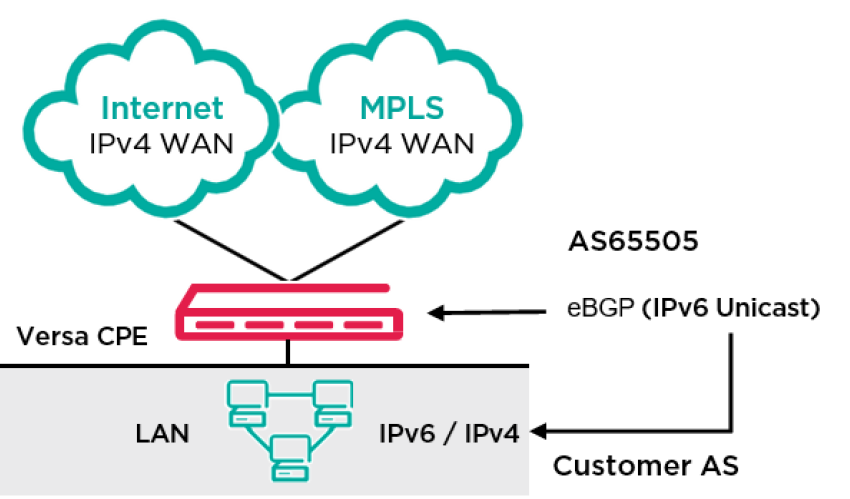
Dynamic routing support in IPv6 Colt SD WAN supports the customer to enable eBGP with IPv6 address family identifier between their Versa CPE and customer LAN device in native IPv6 address.
The BGP parameters of the customer device will be provided by the customer similar to the Dynamic routing IPv4 currently in production.
- Routing Policy requirement
- Customer Local AS Number
- Neighbour IPv6 address
- BGP Password
4.22 IPv6 Support on WAN
IPv6 support on WAN side has been enabled for single CPE, Single internet with IPv6 sites only.
The following types of Internet Access and options are supported:
- Colt IP Access
- 3rd party Internet
- Customer-owned Internet
Local Internet Breakout with basic firewall only has been supported with IPv6 only site.
To support LIB, It is mandatory to have both IPv6 WAN and IPv6 LAN range as NAT46 is not supported.
Note: CIB, Advanced security features with IPv6 only sites are not supported
4.23 SaaS Optimization
This feature provides optimal routing to selective SaaS applications to deliver the best end-user application experience.
In an SD-WAN network, a tenant or organization can reach a SaaS application using multiple WAN links. These WAN links can use different paths and even different transport networks. Because the transmission latency among different paths can vary, it is important to choose the best available path for optimal SaaS application performance.
It improvs Internet traffic steering rules by providing path selection based on user-defined SLA’s such as latency and packet loss to determine the best performance to specific SaaS Applications across:
- Multiple local internet breakout options at the branch and/or
- Both local and centralised internet breakout options
Note: Its available for up to 20 of the most common SaaS applications
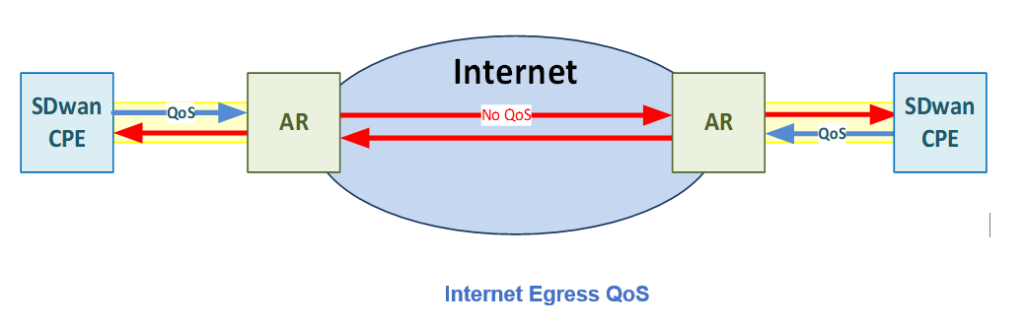
4.24 Internet Egress QoS
Internet Egress QoS is a non-chargeable feature that allows the user to apply Quality of Service (QoS) on the egress (outgoing) traffic of Internet based links of the SDWAN CPE. This means that the user can now apply priority queuing and traffic shaping on Internet connections, allowing for control and prioritization of data traffic.
Internet Egress QoS, unlike QoS over MPLS is not end to end. QoS is not applied ingress (to the CPE), as such the Colt access router will not apply QoS. In case of non-colt internet, Colt and most likely also the customer will have no control over QoS.
Internet Egress QoS only impacts the SDWAN overlay and does not impact on underlay.
Some connection types have asymmetrical speeds (e.g. DSL), the reference bandwidth the customer should use in this case is the upstream (from CPE to Internet) bandwidth.
The configuration of Internet Egress QoS is done via the SDWAN portal only. The functionality can be used by the customers who want to use the capability if required. The actual configuration only impacts the SDWAN CPE and affects the overlay only.
Internet Egress QoS can be configured for ON-NET, OLO or Bring your own (BYO) Internet links with the fixed bandwidths against which the policy can be configured. Internet Egress QoS cannot be configured for Wireless (3G/4G/LTE) WAN connections.
5. NetFlow & IPFIX
NetFlow is used for the collection and monitoring of network traffic flow data generated by NetFlow-enabled routers and switches. It enables analyses of network traffic flow and volume to determine where traffic is coming from, where it is going to, and how much traffic is being generated. NetFlow-enabled routers export traffic statistics as NetFlow records which are then collected by a NetFlow collector.
The collector does that actual traffic analysis and presentation to the user and can take the form of a hardware appliance or software. In our case we use software.
SDWAN CPE log forwarding to Analytics nodes and to third-party NetFlow collectors enables data analysis to provide required reports and data visualization. SDWAN devices export log data in IPFIX and syslog format.
To allow SDWAN devices to send log data to Analytics and third-party collectors, the log export functionality (LEF) is enabled on the device. To export log data from the devices to a NetFlow collector, a NetFlow collector, group, and profile are configured, followed by specifying which data to export.
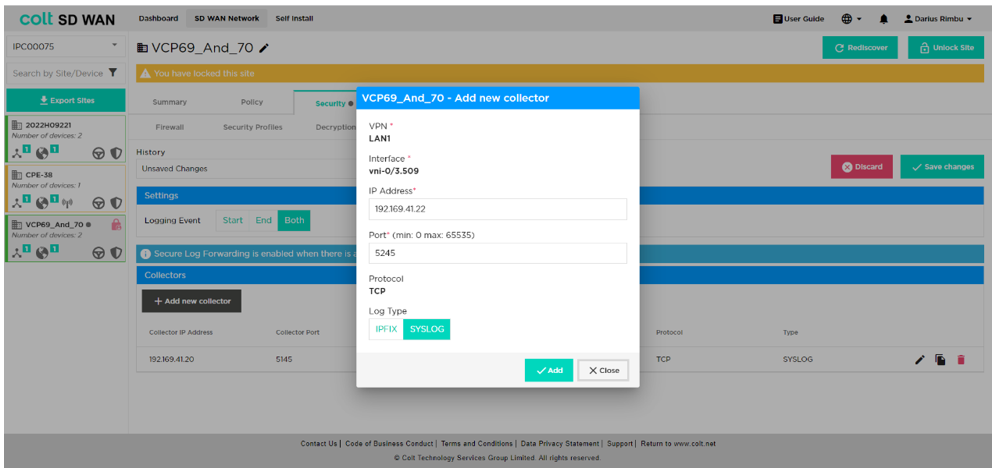
Customers can request flow data in IPFIX format for their NetFlow collector through the SDWAN portal. The IPFIX feature will be available for all customers in the SDWAN portal. Customers need to configure collectors for selected sites/CPE to enable flow monitoring. The IPFIX feature will be enabled at the site level with the capability to copy the relevant IPFIX configurations for some or all sites in the SDWAN Portal.
Following information is captured in the Portal. Up to 5 collectors will be supported per site with following config per collector.
- NetFlow collector IP address– Max 5 (Only IPv4 address is supported by Versa)
- Port ID
- Protocol – TCP/UDP
- VRF instance (By default LAN-1 VRF)
- Frequency of flow record
- Match condition – L4 prefix/Application filter
Customer can choose the frequency at which the flow record will be updated based on what is supported on their collector.
- Start of flow – log data at the start of each session
- End of flow – log data at the end of each session
- Start and End – log data at the start and end of each session
Every 1 minute – log data every 1 minute while the flow is active.
Logging
No additional logging for Colt Analytics has been introduced through this development and no change to existing logging to Colt log servers. Flow logs (traffic monitoring) will be sent directly from CPE to Customer NetFlow collector only.
Only following Versa verified NetFlow collectors are supported
- Solarwinds;
- Cisco Stealthwatch;
- CA Technologies NetFlow
6. Log Forwarding
Overview
There is a growing demand for streaming logs to third party collectors for the purposes of audit, forensics and analytics that can provide actionable intelligence. In the SDWAN context, customers subscribing to firewall features may require firewall service logs for these purposes. The Versa platform is not designed to be a log streaming platform in terms of performance and log segregation perspective so Colt offers a Secure Log Forwarding service based on CPE firewall log forwarding to third part or customer collectors.
The service is an advanced level logging feature, delivered at a branch site level and known as the Secure Log Forwarding (SLF) feature.
The service is configurable via the SDWAN Portal for shipping logs towards up to two customer or third party collectors. The service supports two collectors for TCP streams but limited to only one for UDP streaming.
The service must be enabled in the Security tab in the Portal and is only available if the feature flag is set by Colt.
Supported log formats are Syslog or IPFIX.
Once one site has been configured with the required forwarding configuration, there is a bulk copy capability which can export one site-level configuration to other sites.
Versa CPE Log types
Versa CPE creates and forwards firewall session logs which this includes all enabled NGFW features, such as
- Security Policy
- URL/IP Filtering
- DOS
- IPS
- AntiVirus
- Decryption
For security policy firewall session logs, Colt have not to enabled logging for all sessions, but have enabled session logging for deny rules only as recommended . This configuration default for security features (URL filtering, AV, IDP/IPS) other than security policies and is to reduce risk of overutilizing bandwidth for log forwarding and CPE performance impact.
Caveats and Assumptions:
- This is a best efforts service which is based on the availability of the customer or third party collector.
- Colt do not monitor the SLF service feature over and above the CPE availability included in our SDWAN product.
- The feature flag must be requested to be activated by the customer.
- Configuration of SLF is customer responsibility only, rather than something Colt will configure on request, and must be done via the portal.
- If the SLF is configured to send FW logs towards customer’s syslog servers, this will mean these logs will no longer be present in the Colt deployment of Versa Analytics. This will mean Colt will not have direct visibility of such logs anymore for troubleshooting purposes unless they are provided to Colt by the customer.
Versa Director Log Forwarding (VDLF)
Overview
Along with Versa service logs such as the CPE Security logs as provided by our Secure Log Forwarding (SLF) service option, some customers require their own collection of logs from systems that control the SDWAN for security compliance and audit purposes. For Colt Versa SDWAN services, the Versa Director Audit logs keep track of all changes performed on the Versa Director API or CLI, so can be collected to provide visibility and reporting for changes made to the SDWAN, both by Colt as the service provider and by authorized customer administrators.
The Versa platform is not designed to be a log streaming platform in terms of both performance and log segregation perspective, so Colt offers a separate Director Log Forwarding service (DLF) for this purpose.
It should be noted that the DLF design is a ‘best effort’ service so is not supported by a Colt SLA. This means that the solution can contain single points of failure and may not provide logs during scheduled maintenance of the related platform.
DLF Service
When a Colt customer opts for this feature, the logs generated by the Versa Director platform are exported directly to a customer-provided log monitoring/collection tool.
Examples of the types of logs that customers are as follows:
- Change log for firewall rules
- Change log for QoS
- Change for Traffic Steering
- Change for other features such as DHCP and the logging service itself
An example of the format of the audit logs generated is shown below for a Colt customer:
—–
Dec 7 21:08:51 NV-VD01-MUM [07-Dec-2021 21:08:51.582][,,][INFO][https-jsse-nio-9183-exec-28][VOAE] username@IPC12345, 10.91.194.45:64975, modify, vni:”vni-0/0″, template:CPE-14-xxxxx-MYS-DUAL-MI-P , changeset:devices { template{CPE-14-xxxx-MYS-DUAL-MI-P} { config { interfaces { vni{vni-0/0} { – description TEST-123 + description TEST-1 + ether-options + hold-time } } } } }
—–
Colt Filtering and Forwarding Service
In order to ensure that the logs that are sent are segregated correctly per customer and irrelevant logs generated by the platform are not forwarded, Colt will filter the logs that are forwarded to the customer in the following ways:
- exclude any message containing “Event” : this will remove general platform alarms and events which are used by Colt to provide service assurance and maintenance.
- include any message containing the specific customer “IPC*”; this ensure only logs for the customer in question are sent. ‘IPC*’ is the format used by Colt in the Versa Director to identify different tenants on the platform, e.g. in the example log provided above, ‘IPC12345’ ensures only logs for that specific customer are forwarded by the service.
- A separate log forwarding server is used for the purpose of delivering the exclusions and ensuring the customer log forwarding segregation via appropriate scripting and processing, since Versa Director is not able to provide this filtering capability natively
Streaming Requirements
In order to securely stream the logs to the customer platform, Colt will initiate a TLS Encryption between the log forwarding server and the customer platform which should be reachable via a public IP address. Details of this encryption will be finalised with the customer during the project initiation, including the required process for Certificate Management and Renewal process of the certificates. TheSD WAN Gateway customer will be required to provide a certificate for this purpose and the detail of this will be gathered by the account team.
Caveats and Assumptions
- The output from the service has been tested with syslog-ng as the recipient collector but any stable log management system should be able to receive and process the logs without restriction
- This is a ‘best efforts’ service which is based on the availability of the customer or third party collector
- Colt do not monitor the DLF service feature over and above the Versa Director availability included in our SDWAN product
- The feature must be requested by the customer via our Colt Sales Engineer/Account Executive
- For clarity, Colt will not provide any support on the contents of the log that is being received by the customer. Colt will provide support if the logs are not being received by a customer but analysis and interpretation of the contents are the responsibility of the customer only
- Please note that by the nature of the service being associated with changes to the Versa Director, there may be no logs generated for extended periods
- It is the customer’s responsibility to initiate any required Certificate renewal process on expiry
- The output from the service has been tested with syslog-ng as the recipient collector but any stable log management system should be able to receive and process the logs without restriction
7. SD WAN Gateway
SD WAN gateways are primarily used to provide following functions:
- As transit hub for internetworking between SD WAN and Non SD WAN sites. This is currently used for interworking with legacy MPLS VPN sites.
- As an SD WAN hub for connecting SD Wan sites on disjoint transport networks e.g. an MPLS only site and internet site
Colt’s Versa SD WAN solution supports following types of SD WAN Gateways:
- Shared SD WAN Gateway (Default option): SD WAN shared gateways are multi-tenant FlexVNF instances hosted by Colt in the SD WAN nodes. Shared SD WAN gateways are available on the shared Versa platform. These gateways come with 1+1 redundancy and provide 100mbps CIR bandwidth per customer. Allocation of shared gateways is determined based on internal rules, such as the shortest path and available capacity.
- Dedicated Gateway: SD WAN customer dedicated gateways are hosted by Colt as VNF on the Colt NFVI platform. These dedicated gateways can be available on either a shared or a customer’s dedicated Versa platform. They come with standard redundancy options of 1+1, 2+0, and 2+1, with a bespoke 2+2 redundancy available within regions such as Europe, the US, or Asia. The dedicated gateways offer bandwidth options of 1G, 2G, or 5G, and the gateway VNF flavour is selected based on the chosen bandwidth.
- Customer branch as a Gateway: This gateway option provides customers with flexibility to select one or more of their SD WAN sites as SD WAN gateways.
SD WAN gateway guidelines:
- Customers can now choose different SDWAN Gateway options for each region (Eu, USA, or Asia) as part of their overall SDWAN network.
- Customers can not mix Dedicated and Shared SDWAN Gateway options under a single SDWAN network.
- Customers must choose only one type of SDWAN Gateway option for each region. No mix & match allowed.
- As part of their SDWAN network, following are the ONLY allowed combination of SD WAN gateways options customer can choose in different regions,
- “Shared SDWAN Gateways” and “Customer Branch as SDWAN Gateways”.
- “Dedicated SDWAN Gateways” and “Customer Branch as SDWAN Gateways”.
- Possible number of customer branches as gateways in a region:
- Minimum 2 or Maximum 4 in case of single CPE SD WAN sites
- Minimum 1 or Maximum 2 in case of dual CPE SD WAN sites
- Customer branch as SDWAN GW must be on-boarded before onboarding any other branch CPE in the same region.
8. SD WAN QoS
The Colt SD-WAN platform allows customers to effortlessly monitor and manage their network through a user-friendly self-service portal. This platform enables users to set up and manage routing policies, enhancing agility, security, and IT responsiveness to business needs.
As part of our roadmap, we have developed IP QoS and CIB management features in our portal. Customers can manage QoS policies independently through the portal.
Colt SD WAN Qos Overview
- Customer QoS Classes + Routing & Management
- Premium (EF)
- Business-1 (AF31)
- Business-2 (AF21)
- Business-3 (AF11)
- Standard (Best Effort)
- Management & Routing (AF41)
- QoS available on MPLS circuits only – traffic prioritised on MPLS WAN and across MPLS underlay
- DSCP rw (read-write) applied to inner and outer packet (Tunnel rw inner-to-outer)
- Customer defines (Currently in the order)
- % Bandwidth for each class, max 50% for premium with 5% reserved for management/routing
- Rules to map traffic to different QoS classes
- Match on source/destination ip port, protocol, or DSCP
- Match on Application (incl. source/destination ip)
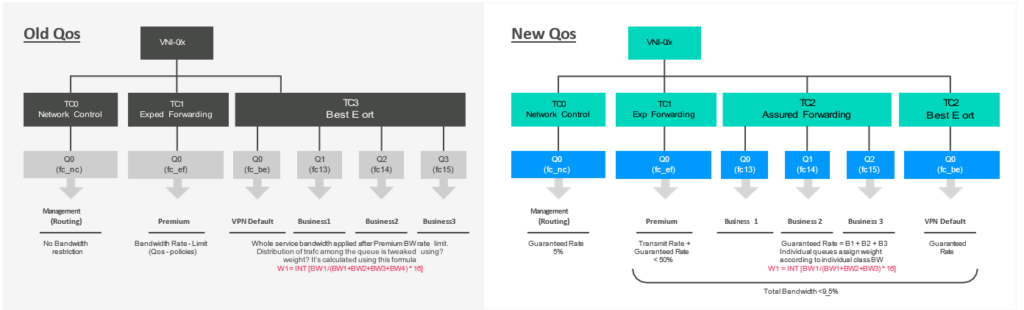
- Recommendation – Voice & Video should be in Premium (TC1) & Data in Business 1, 2, 3 (TC2)
- SD WAN QoS guarantees the BW for each Traffic class
- SD WAN QOS gives flexibility of guaranteed BW for each Traffic class
- SD WAN QOS provides easy management through portal
- SD WAN QOS provides better reporting
9. Central Internet Breakout
The central internet breakout feature allows customer to purchase a shared/Dedicated/SD WAN branch infrastructure gateway that enables diverse paths for applications to breakout to the internet under policy.
- Shared GW – These gateways are traffic shaped to limit available bandwidth per customer
- Dedicated GW – These gateways provides higher bandwidths, high resiliency and Interworking.
- Customer branch as a Gateway: This gateway option provides customers with flexibility to select one or more of their SD WAN sites as SD WAN gateways
The SD WAN Gateway will be configured as Central Internet break-out for Customers requesting CIB functionality through ordering system to
- Provide basic Internet access to MPLS only sites.
- Provide Internet backup over MPLS for hybrid sites.
- Application Based Internet Breakout
Existing SDWAN gateways will be configured to provide Internet access for all the SDWAN sites by default for the Customers enabled with CIB.
P.S. Ensure traffic classification does not conflict with SDWAN policy; if it does, SDWAN policy will override Internet policy.
9.1 Application Based Internet Breakout
Application-based internet breakout enables users to direct specific application traffic to a designated Internet uplink or CIB according to their business policies.
The Colt SD WAN portal enables customers to configure application-based internet breakout policies as detailed below:
- SDWAN policy with Next-hop priorities will be used in order to steer Internet traffic based on Application type.
- SDWAN policy with Next-hop definition will override the routing decisions and selectively send traffic over preferred Internet uplink or CIB.
- Traffic for applications not specified in SDWAN policy will be forwarded based on routing table lookup
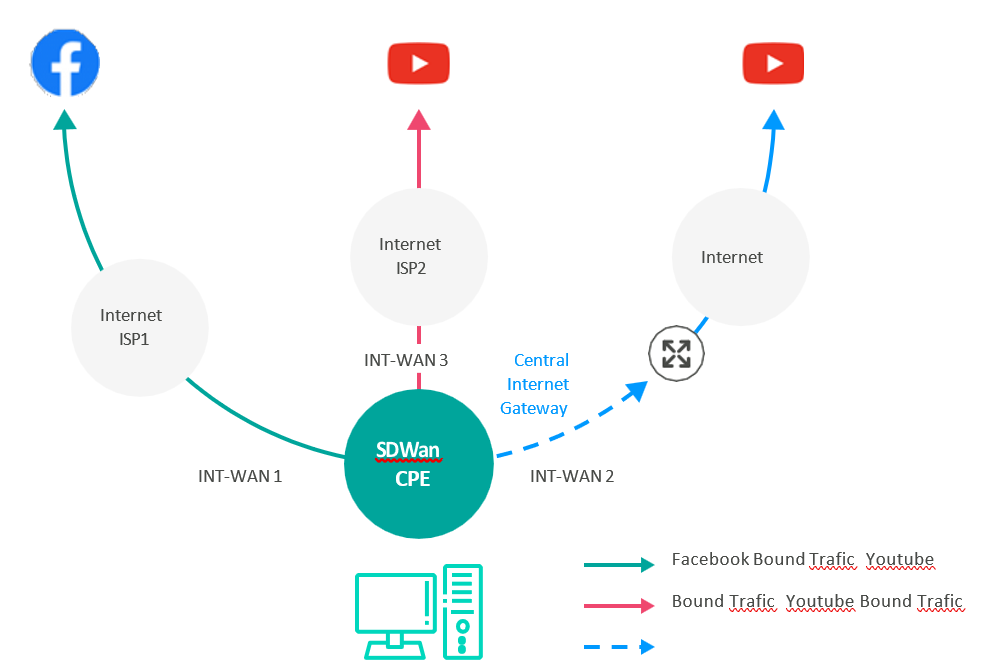
10. Security+
Colt SD WAN Security+ feature set is ideal for Customers needing protection against modern web-based security threats like malware attacks, targeted attacks, application layer attacks; these attacks exploit weaknesses in applications, rather than weaknesses in networking components and services which are traditional attacks and can be prevented by a stateful firewalls.
Security+ is a powerful on prem security tool which encompasses NGFW & UTM (unified Threat Management Features). When customer upgrades to Security+ automatically NGFW & UTM features are enabled. UTM comprises are key security features such as
- Intrusion Detection(IDS)
- Intrusion Protection(IPS)
- Anti-Virus(AV)
Intrusion Detection & Protection (IDS & IPS)
A security vulnerability is an unintended flaw that allows malicious users to surreptitiously attack a network. Attackers can exploit such vulnerabilities to break into and damage the network by changing, destroying, or stealing secured or confidential information, or by installing malware.
To protect a network against security vulnerabilities, Versa unified threat management (UTM) capabilities include intrusion detection and prevention (IDP). IDP is a pre-emptive approach to network security that identifies potential threats and responds to them based on user-defined policy.
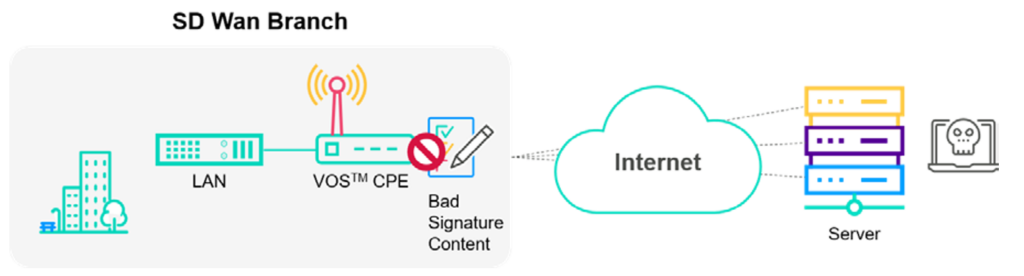
Intrusion Detection (IDS)
- Signature Detection
- Alert Administrator
Intrusion Protection (IPS)
- Alert Administrator
- Drop Malicious Packets
- Blocking the source address & Reset
Client Protection
Client traffic is the request which gets initiated to the server, which is hosting services, the service could be web, mail, file service etc., In such case the protection is applied to prevent client from downloading any virus or preventing from any intrusions.
Server Protection
For those customers who wish to publish their services to the internet world, there should be a protection applied for such incoming malicious attempts. In such case the protection can be applied in the firewall rule where access is enabled for the server. In this way all incoming traffic to the services get inspected through IDP & AV and the clean traffic gets forwarded to the server.
Caveats For AV and IPS
- Not supported for MPLS only sites and towards SDWAN traffic now,
- Limited to Versa CPE models 220,810 and 1800 only
- Logging limitations due to existing infrastructure capacity constraints
- AV/IPS/SSL decryption Impacts Performance due to the CPU intensive process involved on this.
- AV is not supported with protocol MAPI currently.
- SNAT support for East-west firewall rule is limited to single CPE deployment
- SNAT,DNAT,DDOS is supported only with single cpe topologies now.
Antivirus Protection
Our antivirus engine which can scan the live traffic and it scans the files after the entire file is received. When the file is extracted and buffered, the file is trans- ferred to the destination except the last data packet. Once the virus scan is performed the rest of the file is transferred or blocked to the destination depending upon the action defined in the policy.
- NGFW policy with Antivirus profile: We can configure one or more antivirus profiles and be configured under the NGFW access policy rules. it’s enforced only for the traffic that matches that rule.
- Direction: We support the antivirus scanning of file extracting only from upload or download direction as default. As on option we should be able to provide both directions scanning too.
- Protocols & File Type: We support file extraction from all protocols and file types supported by versa
Protocols:
- Web traffic sent using FTP and HTTP
- Email traffic sent use IMAP,POP3, and SMTP
| 7zip | Docx | mach_o | mpeg | class | tar | c |
| Cpp | Lha | php | ppptx | gif | xml | exe |
| Html | Msoffice | rtf | torrent | mdi | coff | targa |
| mp3 | Rar | xls | appleplist | doc | pl | gzip |
| Ppt | Wav | cab | reg | jpeg | rm | mov |
| Tif | Bat | flv | wmf | msi | wmv | zip |
| android | Dwg | mdb | bmp | psd | txt | |
| Dll | Lnk | pif | elf | lzh | avi | |
| Jar | sh | xlsx | Pgp | png |
- Performance Benchmark: Portal shall display the top malwares, antivirus attacks on the traffic flowing on the network. It shall also provide the attackers, victims and applications infected via analytics. We have the alerting mechanism to send real time warning upon any security vulnerability observed (e.g. Virus found in transmitting / receiving file) Similar to IDP caveat there is limitation in terms of storing logs and performing historical or real time intelligent analysis of traffic to alert the customers and needs to be considered/ vetted and provided to customer later in the product roadmap.
11. NGFW
Colt SD WAN uses an integrated Next Generation firewall that offers advanced firewall capabilities integrated with SDWAN router, the functionality can be configured via Colt SDWAN portal. The Advanced firewall capabilities allow the customer to connect separate LAN and DMZ networks to the SD WAN CPE and is used in combination with the local Internet breakout feature.
Colt also offers The Denial of Service (DoS) protection feature with Versa SDWAN. It is used to protect services on the customer LAN or DMZ that are exposed to the Internet e.g. web servers, mail servers. It is only supported in combination with the DMZ / destination NAT feature for the traffic from the Internet towards the LAN/DMZ.
P.S: SD Wan portal supports DDoS policy management for single CPE topologies as standard IP Filtering
Traffic passing through the network may have IP addresses that are associated with a bad reputation and that may cause security risk to your network. To block these IP ad- dresses based on IP address reputation and IP address metadata such as geolocation, you can configure IP address filtering profiles and then associate them with security policy. IP filtering is based on the reputation associated with an IP address and its geo- location where you can filter traffic based on IP reputation and IP address metadata (that is, geolocation). Versa Networks provides an IP reputation feed that is updated both through Spack updates. It will be supported from NGFW service enabled CPEs.
Following are the requirements to be referred for development of IP filtering solution
NGFW policy with IP filtering profile:
We can configure one or more Ip-filtering profiles and are configured under the NGFW access policy rules. It is enforced for the traffic that matches that rule.
IP filtering Profiles supports user defined profiles in which it supports to create rules for both IP reputation and Geolocation based filtering. Each IP filtering profile object consists of the following:
- Rules for geolocation-based actions- It will be supported with either one or multiple actions in one profile
- Rules for IP reputation–based actions -It will be supported with either one or multiple actions in one profile
IP reputation:
IP filter profile supports using the following predefined IP reputations:
- BotNets
- Denial of service
- Phishing
- Proxy
- Reputation
- Scanners
- Spam sources
- Web attacks
- Windows exploits
Geolocation
Colt provides a list of predefined regions that provided by vendor versa which you can use to create IP filter profiles based on geolocation.
In addition, it will support matching the IP address based on the following match criteria:
- Source IP address
- Destination IP address
- Source or destination IP address
- Source and destination IP address
You can enforce the following actions when a session’s IP address matches the condi- tions in the IP filtering profile:
- Allow
- Alert
- Drop packet
- Drop session
- Reset
Note: Default action will be in effect, if the user defined actions are not matched for the customer traffic.(Similar like URLF)
IP filtering profile will be override though we have URLF profiles matching the same traffic pattern. So, it must be created accordingly to meet customer requirements through SDWAN portal.
IP filtering analytics requirements:
- IP-Filter monitoring fields
- IP-Filtering Analytics
Note in scope:
- Predefined IP filtering profiles
- Override of URLF profile in IP filtering profile.
- Custom IP reputation action
- Whitelisting and Blacklisting of IP address in IP Filtering profile
URL Filtering
To address the customer demand on ever growing SDWAN space, besides other features such as firewall, AAR etc. It is imperative need for customers to use web safely for business needs. URL filtering is one of best features available in the market which is provided by many vendors such as Versa, Zscaler, Fortinet, Barracuda and Palo Alto etc.
URL filtering is mainly used for blocking certain URL from loading on company’s network, If an employee would attempt to visit this URL, either by entering it manually or clicking a link in a search engine, they will be redirected to a page notifying the content is blocked. URL filtering relies on filtering databases that classify URLs by topic; each topic in this system is either “blocked” or “allowed.”
Administrators are capable of setting up blocklists for individual URLs, blocking specific websites they know to be dangerous or harmful. More broadly, administrators can block entire URL categories, block listing entire groups of websites at once.
The Colt SDWAN URL filtering solution is a powerful next generation firewall feature that is used to monitor and control how users access the web over HTTP and HTTPS. This feature can be used to gain complete visibility and control of the traffic that traverses your firewall and will be able to safely enable and control how your users access the web. We use versa URLF NG firewall service to enable URLF feature in which it can perform URL categories and reputation including customer-defined, Cloud-based lookups, Policy trigger based on URL profile (blacklist, whitelist, category and reputation) action include allow, alert, block and Captive portal response including customer defined actions include block, ask, Override and justify by URLF profile.
Sales to capture the URL filtering requirement in EOF at site level and URLF feature is enabled for all the Customers in SDWAN portal. Customers can configure URL rules for selected sites/CPE to enable URLF under firewall.
Category Based Filtering
Security access rule with URLF profile for ex. allowing Social sites category and blocking job sites.
Reputation Based Filtering
Security access rule with URLF profile for ex. allowing Trustworthy & Low risk reputation sites and blocking high risk and suspicious reputation sites
URL Filtering Setup
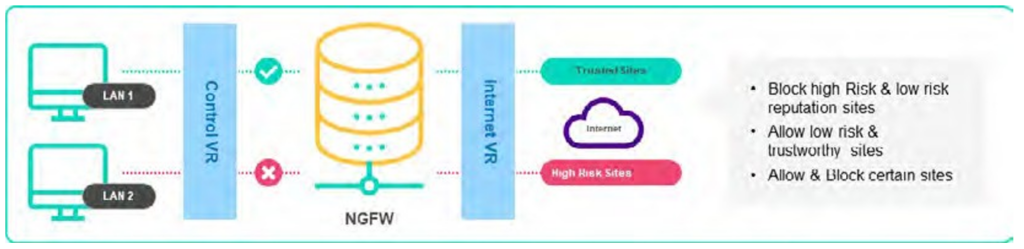
Topologies supported.
Please find the various single CPE topologies supported with standard deployments as mentioned below,
- Internet Only Single CPE (INT)
- Internet Only Single CPE (LTE)
- Hybrid CPE Single CPE (INT & MPLS)
- Hybrid CPE Single CPE (LTE & MPLS)
- Dual Internet Single CPE (INT & INT)
- Dual Internet Single CPE (INT & LTE)
- SINGLE-CPE-DUAL-INTERNET-HYBRID-LTE (New MWL)
Please find the Dual CPE topologies supported with standard deployments as mentioned below,
- Dual Internet Dual CPE (INT & INT)
- Dual Internet Dual CPE (INT & LTE)
- Hybrid Dual CPE (INT & MPLS)
- HYBBRID Dual CPE (LTE & MPLS)
- DUAL-CPE-DUAL-INTERNET-HYBRID-LTE-PRI (New MWL)
- DUAL-CPE-DUAL-MPLS-HYBRID-LTE-PRI (New MWL)
- DUAL-CPE-TRIPLE-INTERNET-LTE (New MWL)
- DUAL-CPE-TRIPLE-INTERNET (New MWL)
- DUAL-CPE-DUAL-INTERNET-HYBRID (New MWL)
- DUAL-CPE-DUAL-MPLS-HYBRID (New MWL)
- DUAL-CPE-DUAL-HYBRID-DUAL LTE (New MWL)
- DUAL-CPE-QUAD-INTERNET (New MWL)
- DUAL-CPE-TRIPLE-INTERNET-HYBRID (New MWL)
URLF filtering has been developed and productized as below:
URLF Phase -1
Under this phase for all standard customers the following features are developed
- Filtering of Web traffic for standard/Bespoke CPEs based on the Whitelist, Black list, Category and Reputation With URLF actions supported
- Alert
- Allow
- Block.
URLF Phase -2
Under this phase for all standard customers the following features are developed
- Filtering of Web traffic based on the Whitelist, Backlist, Category and reputation With URF actions supported
- Alert
- Allow
- Block
- Ask
- Justify along with Captive portal and SSL decryption.
URLF Phase -3 & 4
Under this phase for all standard customers the following features are developed
- Filtering of Web traffic based on the Whitelist, Black list, Category and reputation With URLF actions supported
- Alert
- Allow
- Block
- Ask
- Justify
- User defined action (Override/Ask/Block/Justify) along with Captive portal ,
- SSL decryption
- SSL-decryption Bypass feature
Bulk URLs upload feature in portal.
12. Colt SASE Solution
Colt offers various security services integrated with network services based on the SASE (Secure Access Service Edge) model. Colt provides a single-vendor option with Versa SDWAN and Versa SASE integration, as well as a multi-vendor SASE option where Versa is the SDWAN vendor integrated with Zscaler as the SSE (Secure Service Edge) vendor.
These service options allow our customers to choose the appropriate level of security service integrations with the SDWAN service.
12.1 Versa Hosted SASE Solution
Versa cloud hosted SASE services offering provides users with a secure connection to the enterprise applications hosted on the private corporate network as well as Cloud/SaaS.
Colt SASE Solution has productized following Versa SASE services:
- SD WAN Remote Access (aka VSA/VSPA)
- SD WAN Remote Access + SASE Gateway Solution (Bundle)
- SASE Gateway Solution (aka SWG/VSIA)
SD WAN Remote Access
- Digital Transformation has accelerated the migration of enterprise applications and workloads from an enterprise datacentre to a variety of public clouds and/or SaaS services.
- Users are connecting from everywhere : COVID-19 has changed the workplace to a new normal where employees Work from Anywhere, and the employee’s home is the new office.
- Moving to SASE : Flexibility with a cloud-based infrastructure, where a customer can implement and deliver security services such as threat prevention, web filtering, sandboxing, DNS security, credential theft prevention, data loss prevention
To meet customer demand and part of adopting SASE, Colt uses Versa Secure Private Access as a feature of SD WAN. Colt’s SD WAN Remote Access is the one of the industry’s first solution to deliver the leading Secure SD-WAN services and private connectivity for remote employees. With this solution, employees can now securely connect to applications in both the private and public clouds as part of Remote Access Service Edge services.
With entire workforce connecting remotely through different devices during Covid-19 has created an immediate demand for remote working solutions that can
- Scale
- Include security
- Deliver traffic steering and conditioning
- Offer easy to setup, manage and operate solution
Provide visibility and insight to network performance
A new network model is needed to deliver remote working that is scalable, flexible, agile, and secure over a resilient and reliable network. With users remotely trying to access cloud-hosted applications, on-premises applications, Virtual desktop applications, together with SaaS application such as Salesforce and Office365, security and performance demands skyrocket.
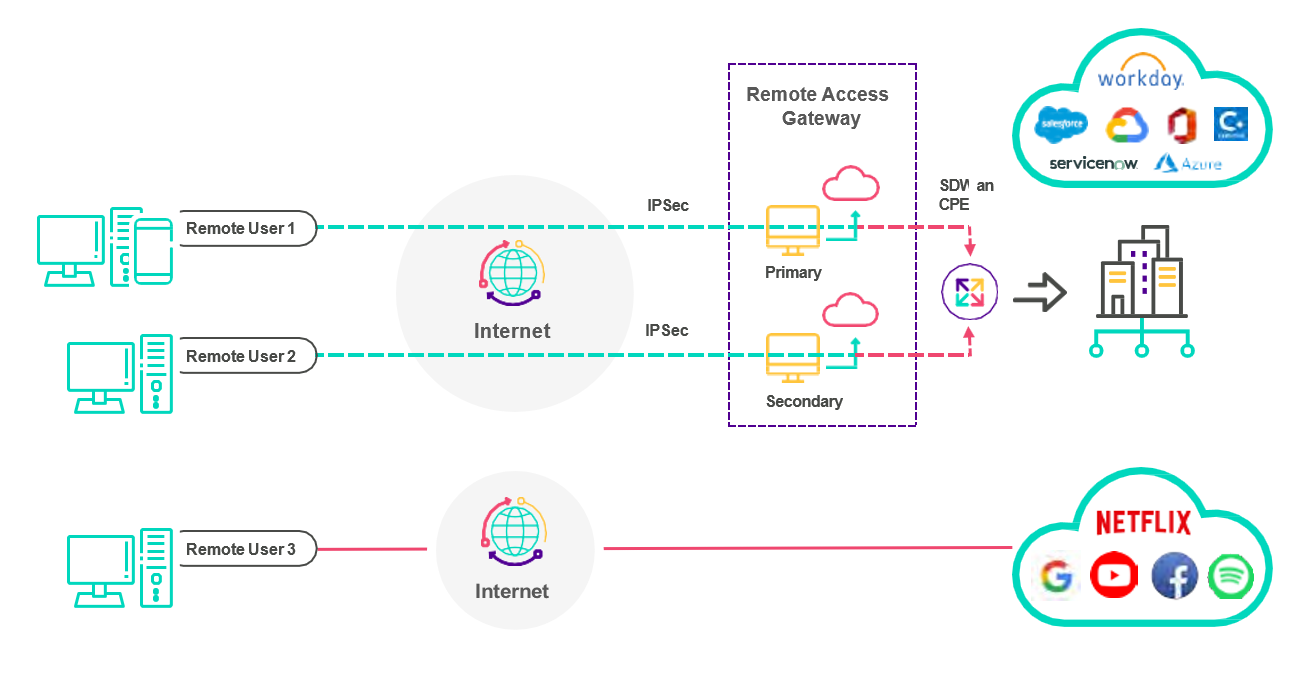
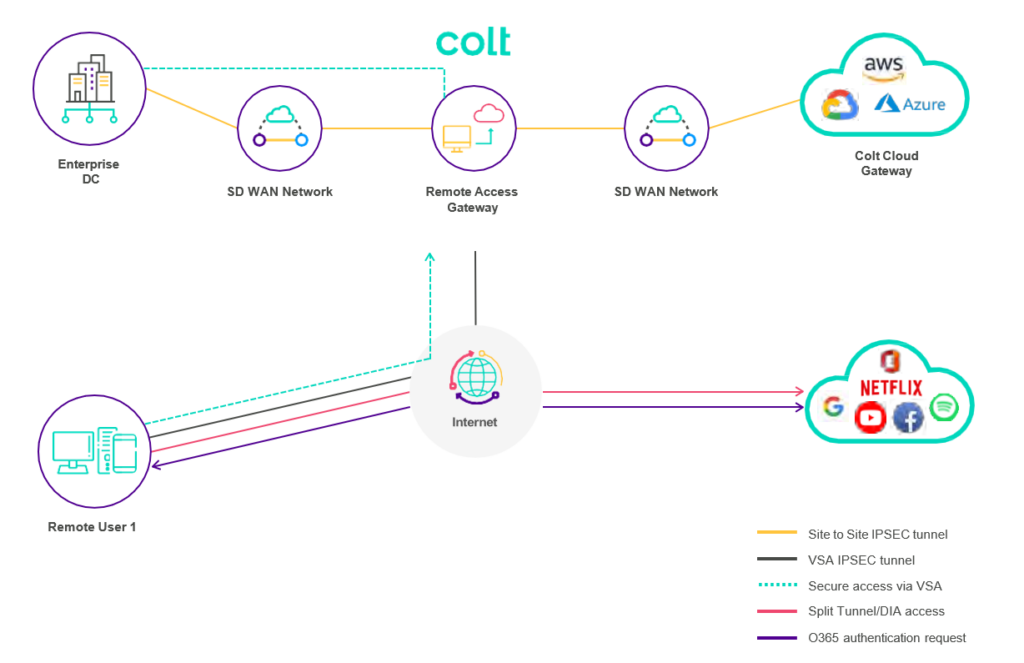
Service Components
Remote Access (VSA) is a distributed solution to connect distributed users to enterprise applications. The applications can be distributed across private cloud, enterprise data centres and public cloud. The Versa Secure Access Solution consists of:
Remote Access Gateways (VCG) are based on FlexVNF/VOS platform. They are globally distributed to provide distributed secure on-ramps for access to enterprise applications. Gateways authenticate users, authorize the application access and secure the enterprise network from external threats.
Remote Access (VSA) Client is software agent/application that runs on and extends SDWAN to client devices (i.e.: Windows, MacOS computers & mobile devices). Remote Access Client creates a secure and encrypted connection from remote device to the Versa Cloud Gateway. Upon authentication and access authorization through the Versa Cloud Gateway, users with VSAC can securely connect to enterprise applications in private cloud.
Remote Access (VSA) CPE provides connectivity to Colt SD-WAN fabric to Remote users to access on-prem applications. 2 VSA CPE will be installed in Colt Nodes to trombone the traffic to Customer SD-WAN network from Versa cloud gateway.
Remote Access Portal – The Versa SASE Portal, Concerto, is a cloud-based portal that allows configuration and management of SASE deployment. It enables and delivers consistent security policies, network policies, business policies, user policies, and application policies seamlessly between on-premises devices and cloud services.
Benefits
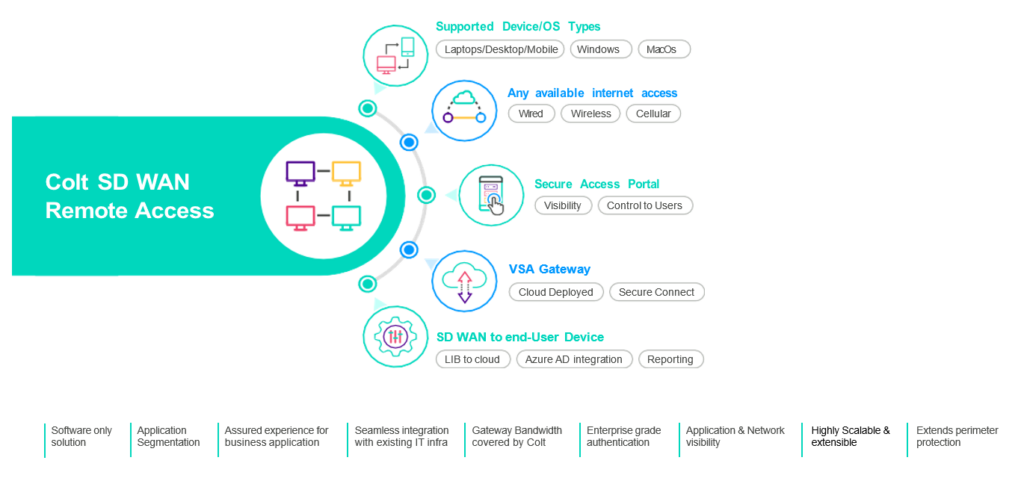
High Level Activities
- Home users (End user) – installs RA client.
- The RA client creates IPsec tunnel to RA Gateway (GW)
- The RA Gateway will have statically configured IPsec tunnels to an SD WAN CPE.
- SD WAN CPE will act as an additional site on the customer SD WAN.
- The CPEs in DC are not in resilient mode, they act separately.
Gateway Locations:
| Region | Country | Location |
|---|---|---|
| North America | USA | San Jose |
| Freemont | ||
| Dallas | ||
| Ashburn | ||
| Miami | ||
| Chicago | ||
| New York | ||
| Ohio | ||
| Canada | Toronto | |
| EMEA | Netherlands | Amsterdam |
| UK | London | |
| Germany | Frankfurt | |
| Saudi Arabia | Jeddah | |
| UAE | Dubai | |
| South Africa | Johannesburg | |
| South America | Brazil | Sao Paulo |
| APAC | Singapore | Singapore |
| Australia | Sydney | |
| Melbourne | ||
| Indonesia | Jakarta | |
| Japan | Tokyo | |
| Hong Kong | Hong Kong | |
| India | Mumbai | |
| Chennai | ||
| Philippines | Manila | |
| China | Beijing | |
| Shanghai |
Customer responsibilities
- Customer IT admin is responsible for handling end user issues
- Customer IT admin to raise trouble ticket with Colt not end user
- Customer is responsible for using the recommended client OS for seamless performance.
Colt SASE Gateway Solution
Covid-19 has changed the way we operate and the new normal is hybrid working. Studies suggest work from anywhere will increase exponentially in next years to come. This brings challenges for enterprise customers to secure their network and data and the other reasons why a enterprise would move to SASE solution are as below
- Internet becoming Corporate Network: The internet is becoming a corporate network for many businesses. SD WAN, enterprise networks are now becoming Hybrid. Opportunity to sell SD WAN.
- Users are connecting from everywhere: Hybrid working is leading to employees working from the office and home. Opportunity to sell Colt remote access or SASE client.
- Need for enhanced Security i.e. SASE: With a cloud-based infrastructure, remote workers further expansion of security is needed. Opportunity to sell Colt SASE gateway product to enhance web security.
To address customers demand we are introducing Colt SASE GW (aka SWG) solution with Remote Access.
Customers can order the SASE solution in the below manner
- SD WAN + Remote Access
- SD WAN + Remote Access + Colt SASE GW solution
- SD WAN + Colt SASE GW solution (Available for Remote/Branch/Both users)
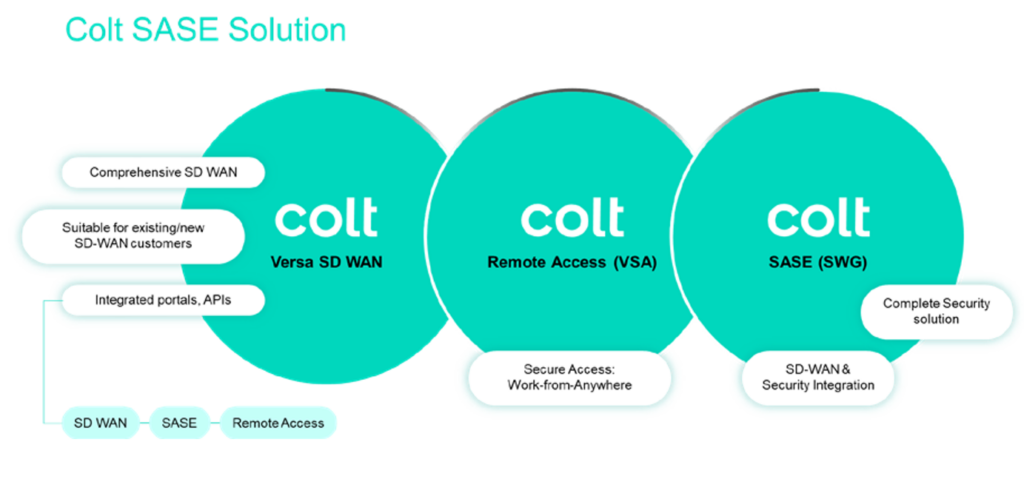
What is Colt SASE Gateway Solution?
The Colt SASE Gateway Solution offers secure internet access to enterprise sites, home offices, and mobile users without compromising performance or user experience. It ensures secure, direct internet connectivity for users irrespective of their location. By utilizing shared threat intelligence, Versa SWG enforces dynamic security measures based on risk and context. We have partnered with Versa to provide both Remote Access and SASE Gateway solutions.
The SASE Gateway solution for SD WAN sites integrates SD WAN functionalities with cloud-native security services, delivering secure access to applications and optimizing network performance for remote and SD WAN site users. It supports policy-based routing, user authentication, and content filtering, thereby enhancing network security and performance. By consolidating network and security functions, the SASE Gateway Solution eliminates the need for multiple point solutions, simplifies management, reduces costs, and improves overall security posture.
SASE gateway for SD WAN sites offers a range of business benefits, including:
- Enhanced Security: SASE integrates security functions directly into the network, providing comprehensive protection against cyberattacks. It enforces granular access controls, identifies and blocks threats, and safeguards data in transit and at rest.
- Simplified Network Management: SASE’s cloud-based architecture eliminates the need for on-premises network appliances and simplifies management, reducing complexity and operational costs.
- Improved User Experience: SASE prioritizes critical applications and optimizes traffic routing, ensuring seamless connectivity for users regardless of location or device.
- Cost Savings: SASE consolidates multiple security and networking solutions into a single, cloud-based platform, reducing hardware, software, and maintenance costs.
- Agility and Scalability: SASE’s cloud-based nature allows for rapid provisioning and scaling to accommodate changing business needs.
- Compliance Enhancement: SASE helps organizations comply with data privacy regulations, such as GDPR and CCPA, by providing granular access controls and data protection mechanisms.
What are the features of Colt SASE Gateway Solution?
Captive Portal/Block Page
Colt SASE Gateway Solution provides informative block page for block actions for URL and IP filtering engines. It can be customized based on customer request. It will be enabled for URL Filtering and IP Filtering with SSL Decryption.
SSL Decryption
SSL Decryption provides protection over encrypted traffic. Once enabled, encrypted traffic from clients is decrypted and malicious content in the traffic can be detected via applying proper security profiles. SSL Decryption is enabled with Colt SASE Gateway Solution certificate by default.
URL Filtering
Colt SASE Gateway Solution offers comprehensive URL Filtering action including Based on reputation, Blacklist-Whitelist, Cloud Lookup. URL filtering policies can be customized. Either predefined or customized URL Filtering policies will be configured based on customer requirement
IP Filtering
IP Filtering profile controls access to web sites based on configured reputation, geolocation, IP white list or IP black list. Either predefined or customized IP Filtering policies will be configured based on customer requirement.
File Filtering
File Filtering provides protection by scanning files that is known by Versa SWG. It takes actions based on file extensions, whitelist/blacklists, predefined file hashes and cloud lookup configurations.
Either predefined or customized File Filtering policies will be configured based on customer requirement.
AV Protection
Colt SASE Gateway Solution provides AV protection by scanning network traffic and understanding malicious content. It takes actions based on configured policies. Either predefined or customized AV Protection policies will be configured based on customer requirement.
IPS Protection
Colt SASE Gateway Solution’s IPS feature provides signature based protection over network traffic. It takes action in case traffic matches with a signature based on configured policies. Either predefined or customized IPS Protection policies will be configured based on customer requirement.
DNS Filtering
DNS Filtering provides protection towards to malicious domains in the internet. Also static whitelist/blacklist of specific domains can be configured in the profile. Either predefined or customized DNS Filtering policies will be configured based on customer requirement.
MDM
CWG supports integration with Microsoft Intune in the scope of MDM. Secure access policies can be built based on client compliance status which will be gathered from Customer Intune solution.
Also it will be possible to build secure access policies based on endpoint protection and OS control on the client. (It is limited with predefined OS and Endpoint protection software on the GW)
NGFW
Colt SASE Gateway Solution offers comprehensive NGFW feature with various configuration options. Policies can be configured based on users, user groups, source/destination, protocol, geo location and application. Security profiles will be enforced in the configured policies.
Logging and Reporting
Logs and reports regarding to security features will be seen in the analytics on Versa SWG VD portal. There will be a retention period for this logs which is not defined yet.
Inline CASB
A Cloud Access Security Broker (CASB) is a cloud-based security function that controls access to cloud applications and data. A CASB enables enterprises to implement security policies governing which users and devices have access to cloud applications and information stored in the cloud.
How does it work?
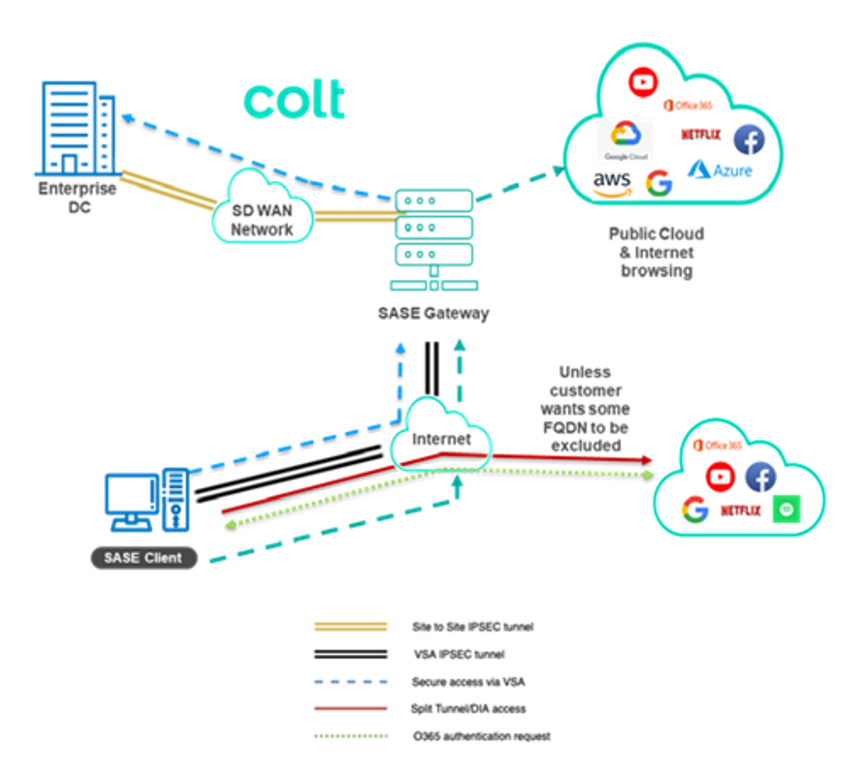
Components:
- SASE Client Software
- SASE Gateway
- SASE Portal (Concerto)
User Flow:
- Home users install the client.
- The SASE client establishes an IPsec tunnel to the RA Gateway (GW) hosted by Versa.
- The SASE Gateway has statically configured IPsec tunnels to Colt Hosted SD WAN CPEs for each customer. All traffic is forwarded to the Versa GW by default.
- Internet breakout occurs at the Versa GW.
- Security policies are enforced.
- Split tunneling traffic can break out directly from the home user to the internet, depending on customer configuration.
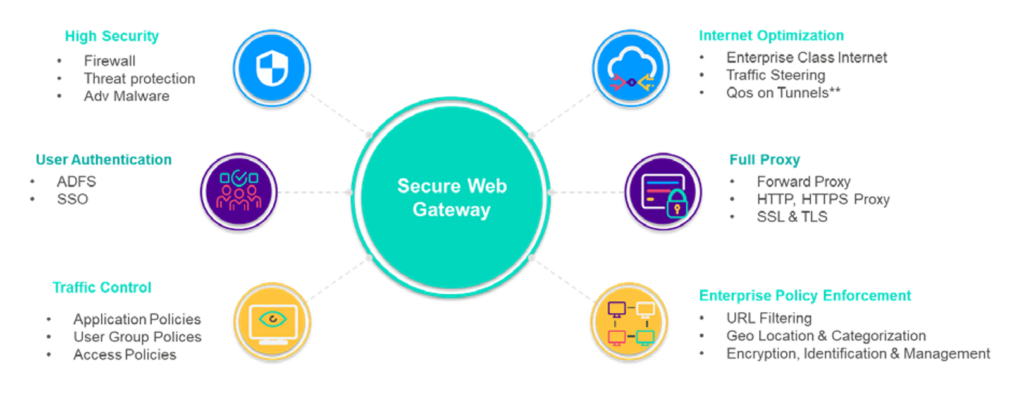
Customers may request and enable on-premises features such as Security, LIB, or CIB alongside the SASE gateway solution. When the SASE gateway is enabled, traffic will by default be routed to the preferred SSE Gateway. Should customers wish to direct specific traffic through LIB, they must configure an Internet traffic steering rule using the SD-WAN Portal to prefer LIB over SASE.
If customers have enabled both on-premises security features and SASE, they must use the SD-WAN portal to configure traffic steering rules and policies to define path preferences.
In general, due to the nature of wireless/LTE WAN uplinks, SASE performance cannot be guaranteed over wireless connections.
Colt SASE Portal (Concerto)
Colt SASE solution provides customers with self-service portal ‘Concerto’ to manage their SASE services. Concerto is cloud-based portal that allows to configure and manage SASE Services.
- For Remote Access (VSA) only, Versa Professional licence type is productised
- For Remote Access (VSA) + Colt SASE Gateway solution (SWG) Bundle, Versa Professional licence type is productised
- For Colt SASE Gateway solution, Versa Professional licence type is productised
Colt has validated and launched Concerto release 12.1.2. Please refer to the following table for key Concerto features validated and productised currently. Link to the SDWAN and SASE Feature Matrix is updated in the ‘References to external documents’ section.
| Feature | Supported | Comment |
|---|---|---|
| User Authentication ADFS integration through SAML | Yes | Single Sign-on not in scope |
| L3 L4 L7 Firewall Security | Yes | DOS Protection not in scope |
| Internet Connection Optimizations | Yes | Comprehensive QoS :QoS on tunnels, traffic shapers not in scope |
| URL Filtering | Yes | |
| IPS | Yes | |
| File Filtering | Yes | |
| Antivirus | Yes | |
| MDM | Yes | |
| Captive Portal / Block Page | Yes | |
| Proxy SSL/TLS Proxy, incl. TLS1.3 | Yes | HTTP, HTTPS Proxy, Forward & Reverse Proxy not in scope |
| DNS Proxy & Security | No | DNS filtering partially |
| Inline CASB | Yes | |
| Network DLP | Yes(with some caveats*) | |
| Network obfuscation (Application & Remote user obfuscation) | Yes | |
| TND (Trusted Network Detection) | No | |
| Trusted/Excluded routes in Trusted/Untrusted networks | No | |
| Custom URL Categories | Yes | |
| Custom Security Actions | Yes | |
| Custom Captive Portal | Yes | |
| IPS Override | Yes | |
| Endpoint Information Protection (EIP) | Yes | |
| SaaS Tenant Control | Yes | |
| User and Device Authentication | Yes | To support ZTNA |
| Advanced Threat Protection | No | |
| Digital Experience Monitoring | Yes | Essential Licence only |
Note: Logs regarding few latest features like EIP, SaaS Tenant Control, Network Obfuscation, TND are not available currently and Versa is working on to fix this.
Concerto portal managed by Versa and accessed through the following link
https://sase-concerto-he1.versanow.net/login
Customers receive their admin/read-only username in the handover letter. Additional Concerto users will be set up upon customer request following their defined process.
As Concerto is Versa managed cloud hosted SASE portal, Colt uses Catch & Dispatch model for any SASE Issue resolution with Versa. Versa provides following SLOs for SASE related issues:
| Priority | Response Time | Resolution Time | Status Updates |
|---|---|---|---|
| P1 | 60 mins | 3 days (workaround in 8 hours) | Every 2 hours |
| P2 | 60 mins | 5 days (work around in 16 hours) | Every 4 hours |
| P3 | 8 hrs | 20 days (work around in 10 days) | Every 5 days |
| P4 | 8 hrs | Best effort | Every 10 days |
Colt SASE customers will have access to two portals: one for Colt SD-WAN (SD WAN Portal – hosted by Colt) and one for Colt SASE (Concerto portal – hosted by Versa). Colt will adhere to Versa’s Concerto release management.
Colt is responsible for handling issues related to the SD WAN Portal, while Versa is responsible for addressing issues associated with the Concerto portal.
Versa will oversee any future upgrades to the Concerto version. Customers will gain access to the latest Concerto Portal once it has been upgraded in production. The Concerto portal user guide is accessible here.
SASE Client
Colt has validated and launched SASE solution based on the following SASE client software versions:
| OS | Version |
|---|---|
| Windows | 7.8.12 |
| MAC | 7.6.4 |
| Android | Latest available in app store |
| iOS | Latest available in app store |
Following SASE client baseline features have been tested by Colt:
| Feature | Description |
|---|---|
| Best GW | Enable by default by Versa Select Best GW for user based on different metrics (*check Versa Service Description for detailed info) |
| Split Tunnel | VSA only tenants Customer static routes + DNS enforcement from Concerto Remote user IP allocation |
| Full Tunnel | VSA + SGW tenants 0/0 + customer DNS enforcement from Concerto Remote user IP allocation |
| Traffic Steering- VSA only | Specific apps can be sent through the tunnel Deny all option TS rules are enforced from Concerto. |
| Traffic Steering- VSA + SWG | Specific apps to be excluded from the tunnel Deny all option TS rules are enforced from Concerto. |
| Always-on | Disconnect option (Never/Interval) Override interval Fail mode (open/close) Enforcement from Concerto required |
| Client Logo URL | Customer Logo will be displayed in the SASE Client Enforcement from Concerto required |
| Display GW | SSE GWs will be displayed on the SASE Client Enforcement from Concerto required |
| Trusted network hostname | SASE client wont established the tunnel when behind a trusted network Enforcement from Concerto required |
| User Authentication | AD integration with SAML Authentication with AD users MFA presented if it is enabled on customer AD |
| NGFW features support | Support for URL Filtering, IP Filtering, Malware Protection, IPS, File Filtering and DNS Filtering |
| End User Notifications | Pop-up notifications for actions taken by Malware Protection and File Filtering |
SASE Add-on features:
Versa Digital Experience Monitoring
As cloud adoption grows, remote work presents challenges for IT and employees. Poor app performance and connectivity issues lead to frustration and inefficiency. IT struggles with limited visibility and control, increasing help desk tickets and operational costs.
Versa Digital Experience Monitoring (DEM) provides comprehensive visibility across devices, networks, and applications. This ensures exceptional user experiences, quick issue resolution, and improved operational efficiency. By monitoring performance metrics, IT teams can proactively address problems and manage expectations, enhancing productivity and reducing costs.
Versa DEM measures and analyzes various segments, allowing IT to pinpoint performance issues quickly and resolve them effectively, ensuring a smooth user experience.
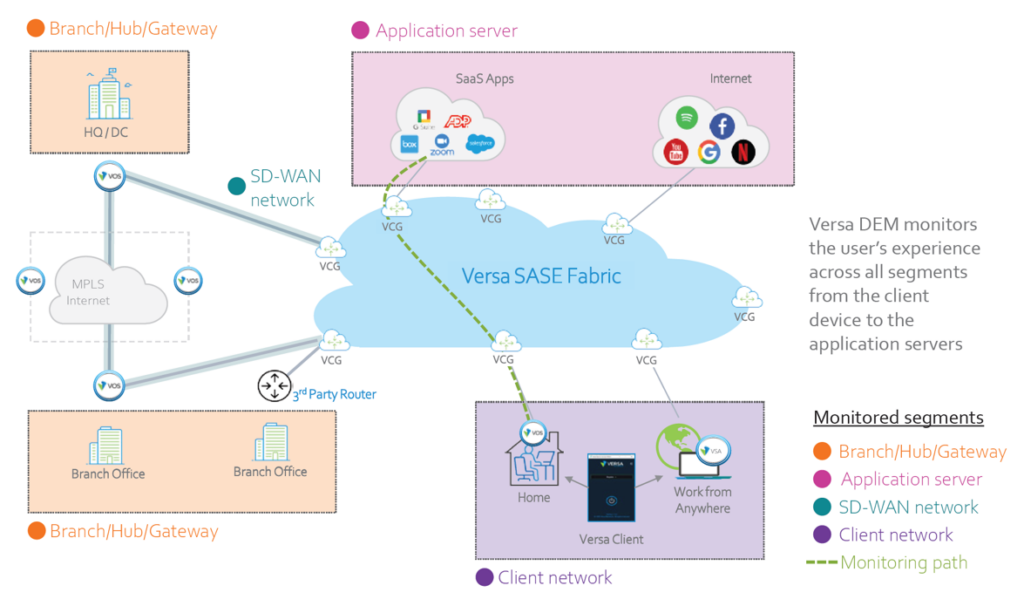
You can enable digital experience monitoring (DEM) on Versa SASE client devices to periodically monitor end-to-end network and application performance for the devices. When DEM is enabled on a device, Versa SASE clients collect the following metrics for a user device:
- Device memory, CPU, disk utilization, and battery life
- WiFi signal strength, and transmit and receive bandwidth per SSID
- Local network segment metrics such as delay, jitter, and packet loss
- Internet segment metrics such as delay, jitter, and loss, both end to end and for each hop level
- Application metrics such as DNS lookup time, TCP and SSL connect times, HTTP latency, time to first and last byte, delay, jitter, and packet loss to application server.
The SASE client exports these metrics to a Versa Analytics cluster, which uses them to derive an experience rank, known as the DEM rank, that ranges from 1 through 100. A value of 1 represents the best experience and 100 represents the worst experience. Versa Analytics DEM maps, charts, and tables provide in-depth information about the experience at the organization, gateway, device, and application levels.
Three components are needed to run Versa DEM:
- Versa Client
- Versa Cloud Gateway or SD-WAN CPE
- Versa Analytics
Versa DEM Licensing:
| DEM Capabilities | Essential | Professional |
|---|---|---|
| Health monitoring of SaaS app connectivity | X | X |
| Health monitoring of custom app connectivity | X | X |
| Health monitoring of access network connectivity | X | X |
| User device health monitoring | X | X |
| Number of apps supported for health monitoring | 3 | 50 |
| App and device health polling interval | 15 min | 5 min |
| Data retention | 2 days | 30 days |
| Advanced probes (AS number, hop-by-hop data) | X | |
| API based access to DEM data | X | |
Versa DEM comes in two tiers: Essential and Professional. Capabilities for the two tiers are listed in the table above. Versa DEM Essential tier is included and available to all Versa SSE customers.
The Professional tier is an add-on license which can be enabled for Versa SSE and SD-WAN customers.
Colt has currently standardised Essential license type only with the following observations/caveats:
- License system (Essential vs Professional) not fully implemented by Versa in Concerto.
- All tenants are enable with Essential by default and limits are not controlled.
- Concerto doesn’t allow to see the type of DEM license in use.
- Limits based on type of license are not implemented. This applies for:
- Control on the number of apps to be enable for DEM.
- Retention period (set by default to 30 days)
- Customs apps are not supported in Concerto 12.1.2
- Interval field in SAC profile need to be removed. Polling interval is fixed per license type.
Versa Data Loss Prevention (DLP)
Data Loss Prevention (DLP) is a SASE security function. DLP detects and prevents data breaches, exfiltration of sensitive data like personal information, credit card or social security numbers.
DLP feature is supported on Concerto to configure following DLP rule types:
- Content Analysis
- File DLP
- Optical Character Recognition(OCR
- Exact Data Match(EDM
- Document Fingerprinting
SASE Operating Model
Following table outlines the key responsibilities of Colt, Versa and Customer during SD WAN & SASE service lifecycle:
| SDWAN/SASE Features | Colt | Versa | Customer |
| Colt SD WAN | – Configures Overlay Provides Underlay – Connectivity – Colt owned/provided – Management & in life support | – Provides overlay core components – VD, VA, Gateways – Maintains Core Components – In-life support | – Provides customer owned underlay connectivity – Management of customer owned connectivity |
| Colt SASE Solution | -Provides selected SASE services (VSA only or VSA+SWG bundle) -Configuration of tunnels -In life support | -Customer onboarding on Concerto -In-life support | -Submit service request -Provides all required details for onboarding -Contact Colt for support queries |
| SASE Portal – Concerto | -Provides portal with Day 1 baselined configuration -User Access Management -Support for Colt baselined features only | -New Feature development -Concerto release management – In-life support | -Security Policy/Rules management through Concerto Portal -Contact colt for any support – Any Firewall configurations on top of Day 1 config |
| SASE Client | -Client control custom configuration -Support for Colt baselined features only | -New Feature development -SASE client release management – In-life support | -Distribute to users any latest SASE client software version available -Manage Secure Access Profile & Policies -Contact Colt for support queries |
SASE Specific Responsibilities
The customer is responsible for providing detailed requirements necessary for the deployment of the Service. Enterprise customers may not resell the Services and may use the Services only within their own sites. Any move or relocation of the SASE service requires the customer to submit a request and receive approval from Colt.
Colt can deliver baselined SASE features through the standard delivery process. Requests for any non-baselined features shall be treated as bespoke and will require further feasibility analysis. Customers can utilize non-baselined features available through the SASE (Concerto) portal or SASE client; however, these features come without support commitments from Colt.
To productize new features in the SASE (Concerto) portal, Colt will first validate them and update the list of baselined features, Day 1 configuration, and respective systems and processes accordingly.
Colt hands over the SASE service to customers with the defined Day 1 configuration on the Concerto portal for baselined features, applicable to the first SD WAN site only.
Day 1 Configuration:
| Colt SASE Day1 / Colt Predefined Configuration | ||||
| Objective | Demonstrate Colt Predefined Configuration for SASE services (VSA/SWG/Bundle) on the Day1 (At the time of service handover) | |||
| Initial/handover State | Managed service (Ready for immediate testing) | |||
| No | Feature/Functionality | Colt Predefined Configuration | ||
| 1 | User and Device Authentication: | |||
| Users/Groups Authentication | SAML authentication configuration with or without Users and User Groups (Based on provided details by the subscriber) | |||
| 2 | Secure Client Access: | |||
| Secure Access | Policy Rule Enforcement | |||
| Secure Client Access | For VSA only solutions: Single Profile with Private Networks ( SDWAN VPN Prefixes) and Private DNS Resolvers Split tunnelling Allow Policy matching all remote users and linked to single Profile (a policy rule per OS: Windows, Apple, Android, Linux) For SWG (or Bundle) solutions: Single Profile with Private Routes( SDWAN VPN Prefixes) & Public/Private DNS Resolvers. Full/Force tunnelling Allow Policy matching all remote users and linked to single Profile (a policy rule per OS: Windows, Apple, Android, Linux) | |||
| 3 | Decryption (Applicable for Subscription SWG or Bundle only ): | |||
| Decryption | Profile | Policy / Description Enforcement | ||
| TLS/SSL Decryption | Certificate Setup: VOS Certificate issued by Versa (Versa self-Signed Certificate ) Inspection Options: Certificate Validation with Online Certificate Status Protocol (OCSP) Server Certificate Actions: block the sites with expired certificate or certificate is received from an untrusted issuer.SSL or TLS Protocol Checks: Alert Unsupported protocol versions, ciphers or key length Decryption Options: TLS Version range – Minimum TLS-1.1 Maximum TLS-1.3 | For all the users & groups, and for Internet Bound traffic, Do Not Decrypt/Inspect the Financial services (URL Categories). Decrypt and Inspect the Traffic other categories | ||
| 4 | Real-Time Protection : Private App Protection (Applicable for Subscription VSA or Bundle only ) | |||
| Private App Protection | Security Enforcement: Allow action for all the private application / SDWAN Network bound traffic (applicable for all the Applications, Users and Groups, Geo locations & services) | |||
| 5 | Real-Time Protection : Internet Protection (Applicable for SWG or Bundle subscription) | |||
| Security Module/Engine | Profile Name | Security Enforcement Action | ||
| URL Filtering | VersaEasy – Block All Standard URLs for Corporate (Versa Predefined) | Preconfigured URL filtering profile controls all web-browsing activity to block: adult_and_pornography, nudity, translation, abused_drugs, gambling, military,phishing_and_other_frauds, violence,weapons,illegal,marijuana, proxy_avoid_and_anonymizers | ||
| File Filtering | VersaEasy – EasyFileFiltering (Versa Predefined) | Preconfigured file filtering profile to inspect following protocols to alert file downloads/uploads: FTP, HTTP, HTTP2, IMAP, MAPI, POP3, SMTP | ||
| IP Filtering | Colt_IPF (User/Colt Defined) | Preconfigured IP Filtering profile to block (Reputation Based Actions): Proxy, Web Attacks, Scanners ,Denial of Service, Reputation, Network, Windows Exploits, BotNets, Spam Sources, Phishing If there are no criteria matched, Default action to enforce, prioritize the URL reputation over the IP reputation | ||
| Malware/AV protection | VersaEasy – Easy Malware Protection (Versa Predefined) | The EasyMalware Protection profile blocks the well-known types of malware such as: Adware, Ransomware, Spyware, Trojans, Unwanted applications, Viruses & Worms | ||
| Intrusion protection system (IPS) | EasyIPS | Versa predefined EasyIPS profile to filter malicious attacks based on signatures or detect vulnerabilities against servers and clients Note – Versa recommends that you use this profile | ||
| SafeSearch | NA | SafeSearch enabled for search results in Google Search, Bing and YouTube | ||
| 6 | Settings: | |||
| Site to Site Tunnels (Read only) | – Tunnels connected to SDWAN Network – Private Networks advertised through BGP (controlled by COLT) | |||
| Captive Portal | Versa Default. Block page presentation for URL Filtering and IP Filtering | |||
| 7 | Users (RBAC) for Concerto Access: | |||
| Usernames with Associated Roles (Enterprise Administrator or Enterprise Operator) & with Enabled Two Factor Authentication. | ||||
Roles and Responsibilities for SASE Services:
Connectivity: Network connectivity is required to utilize SASE Service. Customer may purchase Colt provided connectivity or Customer may provide their own connectivity. Customer is responsible for any underlay connectivity not provided by Colt.
Administration: Colt will manage and provide administration to all SASE services for the Customer with access to SD WAN portal and SASE portal. Colt provides upto 5 administrators and 30 read only users for SASE portal. Customer is responsible to submit any user access management request to Colt. For SD WAN portal once administrators are created, Customer shall manage its user creation and access management.
Reporting: Reporting will be available and limited to what reporting functions are included in the SD WAN portal and SASE portal.
Updates: Colt may periodically require the update of software, hardware, or other components of the SASE service to maintain the latest supported version of the partner services.
Partner can update software versions of SASE portal or SASE client with new features. Colt will support only validated baselined features. Colt will publish the official SASE client version to customers in regular intervals. Incase of any immediate requirement for a change for a Customer, then Colt can check with Versa and publish new version if available. Colt’s network and security engineering teams shall validate the new software versions before standardizing the same. For any interim software release, Colt’s network and security engineering teams shall do the high level assessment to confirm if any testing is required or not. In case if new software version of Concerto portal or SASE client is available, Colt will test and validate the Day 1 configuration defined for baselined features. Colt will only validate SASE client new software version for windows and MAC laptops and not for mobile devices.
Delivery: Colt service delivery will handover the SASE (Concerto) portal to customers with Day 1 configuration defined for baselined features for the first SD WAN site.
Customer Responsibilities: Customer is responsible for defining and managing policies, rules through SD WAN portal. Customer is responsible for defining and managing policies & firewall configurations, rules through SASE portal. Customer is responsible for installing latest available software version of SASE client. In case of Cease, Customer is responsible to remove security configurations through SASE portal and to deactivate SASE service through SD WAN portal.
Versa SASE Service Management Options
Administration and Management. The SASE Service is offered as a Self-Managed service. Colt will provide Customer with access credentials to remotely manage the SASE Service through the SD WAN Portal and SASE portal. Within the SD WAN portal and SASE portal, Customer may make network configuration changes such as traffic steering rules and security policies as required. Colt resources are available 24×7 for support. Colt is not responsible for any SASE features, available through SASE portal, which are not validated and baselined by Colt. Customers can contact colt to raise a ticket for not productized SASE Concerto or SASE Client feature which will go through Catch & Dispatch model to Versa.
Service Exclusions
Support for any features available through SASE portal, which are not validated and baselined by Colt:
- Management of versa managed SDWAN components.
- Management of versa managed SASE components.
- SASE (concerto) portal release management.
SASE client software release management.
12.2 Versa SDWAN with Zscaler SSE Solution
Note: This service is not available to Colt wholesale partners
Colt has adapted its partnership with Zscaler in response to pandemic-driven IT changes. Zscaler’s security model now plays a key role in protecting remote and cloud environments.
Colt is enhancing Zscaler’s Zero Trust Gateway, integrating it with IP Access, IP VPN, and SDWAN services.
By combining Versa’s SDWAN with Zscaler SSE, Colt provides a dual-vendor SASE solution for integrated networking and security globally.
Zscaler SSE Zero Trust Gateway Solution
The Security Service Edge (SSE) model is a collection of integrated, cloud-centric security capabilities that secures access to the web, cloud services, and private applications. SSE capabilities include access control, threat protection, data security, security monitoring, and acceptable use control enforced by network-based and API-based integration. SSE is primarily delivered as a cloud-based service and may include on-premises or agent-based components. In both cases customer traffic is handed off to the cloud, either by the Zscaler Client or App Connector at a site or in the case of this SASE model, by the Versa SDWAN CPE. Therefore the SASE security model integrates the benefits of SSE with SDWAN.
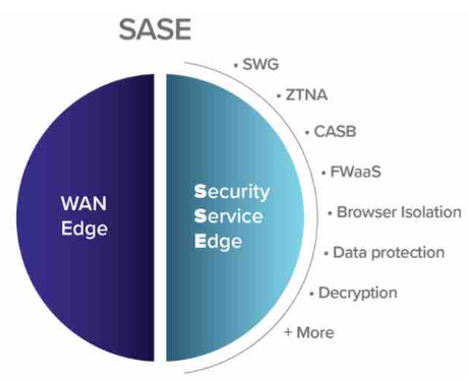
The traffic hand-off from the SDWAN uses tunnels to complete the integration. Colt’s service focusses on these tunnels, proving a managed and monitored service that builds a reliable and performant bridge between the two vendor services.
Features – Zscaler Integration
Zscaler offers several different products including the core services ZIA (Zscaler Internet Access), ZPA (Zscaler Private Access), ZDX (Zscaler Digital Experience). The SSE service integration from Colt focusses on ZIA although ZDX can be added to ZIA as on optional service by Colt customers if they wish. ZPA is also available via the Colt relationship with Zscaler but uses a discrete separate platform so is not detailed in this guide on the integration with Versa SDWAN.
Zscaler Internet Access
The ZIA service is a secure gateway delivered in the cloud as a part of the Zero Trust Exchange™, the world’s largest security cloud. ZIA provides a full security stack with ZIA Service Edges enforcing your policies and protecting your users wherever they are, from the head office to their home offices. The same authentication and policy follow the user, and that policy can be adjusted based on location, device in use, and more to align with corporate Zero Trust policies. User traffic is inspected and forwarded on or blocked according to this defined policy.
To take advantage of this protection, corporate traffic must first route to the nearest ZIA Public Service Edge. Unlike previous centralized models that backhauled traffic to a central location, ZIA is available in 150+ data centres around the world. Many of these data centres are in internet exchange peering points with other cloud infrastructure and application providers, such as Microsoft, Amazon, and Google. Zscaler also peer directly with the Colt network in more than 23 global datacentres to further guarantee optimal traffic performance when using the SASE service.
Each ZIA Service Edge delivers full TLS/SSL interception for all traffic, web proxying, firewall, anti-virus, anti-malware, and security services. The same authentication and policy are applied at each location. Logging is comprehensive and gives you visibility into your entire organization.
Comprehensive details of the extensive Zscaler ZIA features along with all other Zscaler services that can be purchased along with the ZIA service are published by Zscaler at the following location:
https://www.zscaler.com/pricing-and-plans
Connecting to the ZIA Public Service Edge
Customer traffic is therefore forwarded to the Public Service Edge node to use the service and Zscaler support various methods to achieve this:
- Zscaler Client Connector
- GRE Tunnels
- IPSec Tunnels
- PAC Files
- Proxy Chaining
- Zscaler Cloud Connector
As the Colt SASE service integrates SDWAN and SSE, out choice of method here is tunnels and the GRE tunnel option has been proved over many years as the most reliable and performant option and so forms the basis for our service integration.
GRE Tunnels
Generic Routing Encapsulation (GRE) is a tunnelling protocol developed by Cisco that can encapsulate a wide variety of network layer protocols inside virtual point-to-point links or point-to-multipoint links over an IP network. It is basically IP in IP.
Customers should note that A GRE tunnel encapsulates a payload so as such some overhead is created:
- IP header (20 bytes)
- GRE (4bytes to 8 bytes)
Zscaler recommends that you configure two GRE tunnels from an internal router behind the firewall, or the SDWAN device in this case, to the ZIA Public Service Edges: a primary tunnel to a ZIA Public Service Edge in one data centre and a secondary tunnel to a ZIA Public Service Edge in another data centre. Each GRE tunnel can support up to 1 Gbps if the users’ internal IP addresses are not behind a Network Address Translation (NAT) device. This allows the ZIA load balancers to shift traffic to different ZIA enforcement nodes in the same data centre.
Traffic more than 1 Gbps from a single location can be handled by adding more GRE tunnels. Each tunnel must originate from a unique public IP address. In these scenarios, Zscaler recommends that you construct a load balancing strategy that ensures that the same IP address travels across the same tunnel. Failure to do so can cause users to continuously authenticate and they might not be able to access their applications.
Traffic Steering Policy in Versa SDWAN
AS a default configuration for the service, all traffic towards the internet is directed toward the tunnels.
Customers can, however, configure the routing of particular traffic outside the tunnel based on application in the portal. This may be done, for example, when a customer does not want to send Office 365 traffic via the ZIA service.
Versa CPE to Zscaler ZIA General Design Principles:
- A site will have minimum 2 tunnels, each tunnel terminated in a different Public Service Edge
- Tunnels are primary and backup
- Tunnels are configured as maximum 2 per site.
- In case of dual CPE – each tunnel is to be created from a single CPE to reduce single points of failure and increase resiliency
- IPSLA output is used for pro-active monitoring

Versa SDWAN with Zscaler SSE Operating Model
The operating model for this SASE solution splits responsibilities between the customer, Colt and Zscaler in the most sensible manner to provide the fastest time to resolution for all operational elements of the combined service.
The Zscaler services are provided via Colt with the appropriate licensing for users of the Zero Trust Gateway, including Premium Support package and Delivery packages.
Following table outlines the key responsibilities of Colt, Versa and Customer during SD WAN & SASE service lifecycle:
| SDWAN/SSE Features | Colt | Zscaler/Versa | Customer |
|---|---|---|---|
| Colt SD WAN | – Configures Overlay Provides Underlay – Connectivity – Colt owned/provided – Management & in life support | – Versa provides overlay core components – VD, VA, Gateways – Maintains Core Components – In-life support | – Responsible to provide any customer-owned underlay connectivity – Management of customer owned connectivity |
| Zscaler SSE Solution | -In life support with proactive monitoring of tunnels to SDWAN -Raise tickets with Zscaler as and when required | -Zscaler customer onboarding and configuration of tunnels -Zscaler SSE service in-life support | -Submit service requests -Provides all required details for onboarding -Contact Colt for any support related to site connection Contact Zscaler for any support related to Zscaler SSE gateway services |
| Zscaler SSE Portal | -Arranges portal instance setup and correct licensing for service with Zscaler | -Zscaler sets up new instance for customer – In-life support | -Security Policy/Rules management through Zscaler portal -Contact Zscaler for any support |
| Zscaler Client/ App Connector/Branch Connector options | -Zscaler licensing only | -Zscaler supply software and in-life support | -Install any Zscaler software required -Manage policy via portal -Contact Zscaler for any support |
Zscaler SSE Service Management Options.
Administration and Management
The SSE Service is offered with support from Zscaler directly as the experts for the various security functions available and the licensing chosen by the customer.
Colt will provide the management and support for the GRE tunnels while customers will maintain the access credentials to remotely manage the SSE service through the Zscaler portal. Colt resources are available 24×7 for support.
Colt is not responsible for any SSE features available through SASE portal so customers will contact Zscaler when the issue is thought to be a security service-related subject.
Colt is responsible for supporting tunnels to Zscaler from the Versa CPEs and will proactively troubleshoot scenarios when the site is now able to contact either primary of backup Private Service Edge that the site is configured to use, meaning that the Zscaler service is not available for that site.
Colt will also raise a ticket with Zscaler on behalf of the customer if after troubleshooting issues with a site it is not possible to resolve them from the Versa SDWAN CPE. Zscaler will then own the resolution of this ticket and communicate directly with the customer.
Service SLAs
Zscaler Service Level Agreements for both Premium Support and each of the licensed services such as ZIA are published in the following location:
https://www.zscaler.com/legal/sla-support
The published Zscaler SLA will take effect for the relevant contracted services. At the time of writing, for ZIA this means:
‘The SaaS will be available to accept Customer’s Transactions and Sessions 100% of the total hours during every month Customer uses the SaaS (the “ZIA Service Availability Agreement”)’
Colt will recommend the Zscaler Premium Support package which include access to the support services 24 x 7 x 365 via phone / Web Portal / Admin UI.
Service Credits for failure to meet any of the SLAs by Zscaler will result in service credits which will be returned to the customer in the manner published by Zscaler. Again, at the time of writing this would result in a reduction on the next bill due to be paid to Zscaler of the amount of credit due.
The Colt 24 x 7 365 service desk will treat SDWAN alerts raised on Zscaler service availability as a P2 and respond accordingly according to the Colt SLA for that priority, being equivalent to a site on the network being unavailable.
13. Proof Of Concept (PoC) only available for Enterprise segment, or directly for Carrier auto-consumption
Detailed info about PoC can be found in the below doc in showpad:
- Standard SOW (statement of work)
- Standard T&C (PoC specific terms and conditions)
14. Service Delivery
Service delivery consists of the following:
- New service order
- Modifying an existing service
- Out-of-hours changes
- Cessation or cancellation of service
- Demarcation point
14.1 New Service Order
Every service starts with a signed order (document capturing Customer specific requirements and deliverables).
14.2 Modifying an Existing Service
Modifying an existing service consists of the subsequent enabling or disabling of service features, functions and interfaces as well as service changes following initial installation. Service modification orders may have commercial impact, either in the form of one-off/NRC or on-going/MRC.
Modification orders can be grouped under following categories: A, B and C.
Category A
- modifications falling under this category need physical changes to the equipment on which the services are delivered.
- examples include, local access bandwidth upgrade, CPE upgrade to a different version etc.,
Most category A modifications are regarded as new provision in terms of lead times and installations.
Category B
Include remote configuration changes:
- Option 1 (B1) refers to service requests that can be completed within 12 working hours. If a request cannot be handled within 12 working hours, then the delivery time is five working days.
- Option 2 (B2) refers to service requests that can be completed within five or 10 working days.
A committed lead time can only be given for £ 25 sites. Please contact a Colt Account Executive if there is a requirement involving >25 sites
Category C modifications
- Emergency configuration changes can be requested at any time and have a target implementation time of one hour (depends on the change requested) from acceptance of order.
14.3 Out-of-hours Changes
Category B changes can also be requested out-of-hours. Out-of-hours changes must be scheduled and approved in advance, and there is a lead time of 10 working days. There is a charge of €200/hour per scheduled session with a minimum charge of €500 per session.
14.4 Cessation or Cancellation of Service
Request for cessation of service may be subject to a charge in accordance with Colt standard terms and conditions. Should the customer cancel their order during installation, Colt reserves the right to charge for the remaining contract term.
14.5 Demarcation Point
The demarcation point for Colt SD WAN site is Ethernet LAN port on the Colt provided CPE.
15. Service Assurance
Colt provides a high level of service assurance:
- The core network is proactively monitored
- A local language help desk is available 24 hours a day, seven days a week
- Colt Online provides a web-based portal that enables customers to view bills and trouble tickets
Note that this help desk and web-based portal is offered to Colt’s direct customers, not Carrier’s end customer in the case of SD WAN Wholesale. Operation and commercial relationship towards Carrier’s end customer is not part of Colt’s responsibility.
Service assurance includes:
- Customer service
- Service Level Agreement
- Colt Online
- Service monitoring
- Planned maintenance
15.1 Customer Service
Colt has a high quality fibre network that enables the provision of an annual target service availability. The target availability depends on the service taken and the location of customer sites. The fault help desk is available 24 hours a day, seven days a week. Customers can report a fault at any time by contacting the Customer Service Centre and speaking to a representative in their local language.
When the service is provisioned, customers are issued with a unique service reference for each circuit that should always be used when reporting faults. The contact number for fault reporting is specified in the service handover pack.
15.2 Service Level Agreement
Colt offers a comprehensive service level agreement, which pays compensation if agreed targets are not met. Colt’s own global fibre network enables it to provide customers with an annual service availability of up to 99.99%.
Colt’s Terms and Conditions (T&Cs) only apply for our direct customer (Carrier), same for our offered SLAs.
End-customer’s T&Cs and end-customer committed SLAs are Carrier’s responsibility.
Colt Generic T&Cs are specified depending on the type of contract, Enterprise or Reseller. Please consult document Colt Generic T&Cs.
Ask a Colt Account Executive for more information about our SLAs.
15.3 Colt Online
Colt Online is an intuitive, user-friendly application enabling new and existing Colt customers to interact with Colt via a secure Internet connection without the need to speak to a Customer Service Agent or Account Executive.
Note that Colt Online is only accessible for Colt’s direct customers.
For SD WAN Wholesale, the Carrier’s end customer will not have access to Colt Online.
As a result, all features that are only accessible through Colt Online, such as Versa Analytics, will not be available to them.
Every Colt Online customer is provided with an administrator account for a defined user within their organisation. This administrator has full access to the available features for all their customer accounts and sub accounts, including:
- Search and view any bill from the previous six months in .pdf format*
- View the status of any order in the delivery process
- View the status of any ticket (covering faults, enquiries, service requests) in real-time
- Search and view all live services
- View an account dashboard, summarising the four features above
* Not available in Switzerland due to data protection legislation
15.4 Service Monitoring
The Colt backbone network is proactively monitored and maintained which facilitates prompt and efficient remedial action upon any fault detection.
Proactive monitoring is delivered as a standard feature. Customers are proactively informed of Colt opening tickets.
Note that in SD WAN Wholesale, Carrier’s end customers will not receive ticketing information originated from Colt, only Colt’s direct customer (Carrier).
15.5 Planned works and maintenance
In order to ensure performance and security for all customers, Colt occasionally performs maintenance works that may cause customer’s service being unavailable. Colt will endeavour to ensure that such works have minimum impact on Customer’s service. Typically, planned works occur after 20:00 GMT on weekdays.
When planned works are required, customers will normally be notified in advance as per the following timelines:
- When service affecting planned works are necessary, the customer will be notified ten (10) calendar days in advance. Colt will endeavour to ensure that such works will occur during non-working hours, unless a critical intervention is required to maintain network stability.
- For any emergency work, no advance notification will be issued.
- If there are planned works to be undertaken by third parties, Colt will aim to give five (5) calendar days’ notice, dependent on when Colt itself is made aware of the work.
The date and time for planned maintenance cannot be changed or cancelled by the customer.
Colt is not responsible for failure to meet SLA, where such failure is due to a planned maintenance works outage.
For SD WAN Wholesale, Carrier will be responsible for notifying any planned work that may affect their end-customer and ensure they can be carried out.
16. SD WAN Wholesale specifics
16.1 Intro
The objective of Colt’s SD WAN Wholesale service is to deliver a flexible solution that allows Colt to expand without restrictions when selecting the appropriate provider. Additionally, it ensures scalability by enabling us to enhance a customer’s environment with a diverse range of equipment whenever necessary.
Those customers that don’t have an own SD WAN solution and want to cover that gap with a whitelabel choice, can find the perfect match in Colt’s SD WAN Wholesale.
Colt provides the service in a multinational environment, including the equipment, shipment, installation and basic configuration of the devices according to the Carrier instructions during the initial deployment, and will maintain the devices provided (RMAs), together with the connectivity and management plane.
The subsequent management of the service and control platform will be performed by the Carrier/end customer, as for their services and operational model.
16.2 Responsibility split diagrams
The SD WAN Wholesale product is aimed at new or existing wholesale customers.
The Wholesale customer will be looking for an SD WAN product that can be sold to their end customers as a white-label product, as if they were providing the product by themselves.
The SD WAN portal can be either personalized with the Carrier branding or simply provided with no Colt logo or references, this is Carrier’s choice.
The following diagrams show the main responsibilities of each entity, as: acquisition (sale and support)–See diagram below:
service transition – See diagram below
service operations – See diagram below
billing – See diagram below
(only invoicing to Wholesale customer, not end-customer)
service cancellation – See diagram below
change of circumstances – See diagram below
claim – See diagram below
renewal – See diagram below
As per Wholesale segment nature, there needs to be some responsibility split. Here is a proposition for the main tasks and processes:
| BSS | BSS Carrier | Carrier |
| BSS Colt | Colt | |
| OSS | OSS SD Wan | Carrier |
| OSS SD Wan Portal | Carrier or Colt | |
| Carrier Tools | Carrier | |
| Presales | Commercial Management | Carrier |
| HLD | Carrier | |
| Support for HLD | Colt | |
| Bid and negotiation towards end customer | Carrier | |
| Request/order/purchase Underlay | Carrier | |
| Request/order/purchase Overlay | Carrier | |
| Deployment | LLD (design with End Customer) | Carrier |
| LLD (Templates and configuration) | Carrier or Colt | |
| Management and control platform | Colt | |
| Supply, Installation, CPEs | Colt | |
| Configuration of initial tempaltes/policies | Colt | |
| Management | CPEs maintenance | Colt |
| RMA detection | Carrier | |
| Portal Management | Carrier or Colt | |
| L0, L1 | Carrier | |
| L2, L3 | Colt | |
| Change (request, notification to and customer) | Carrier | |
| Risk Analysis | Carrier | |
| Changes execution | Carrier or Colt | |
| Supply | Colt | |
| Installation | Colt | |
| Fullfilment | Basic Configuration per site | Colt |
| Underlay configuration | Carrier or Colt | |
| Underlay Network Monitoring management | Carrier or Colt | |
| Failures management | Carrier or Colt | |
| OSS Underlay | Carrier or Colt |
For further details of the different responsibilities, please contact a Colt Account Executive.
17. Commercials
17.1 Contract period
The standard contract term is between one year and five years.
17.2 Billing
Colt offers a range of billing options including monthly billing. Bills are available on paper or on CDROM. Each bill contains summary sheet and further reports detailing the following charge types:
- Site installation and rental charges
- Any other charges and credits
- Discounts by service, if applicable
Charges will be billed on a per site basis as each site is provisioned. Bills are calculated on a pro rata daily basis. Bills will be raised for the entire network in the country in which the service was contracted.
Billing is only meant for direct customer (Carrier in the Wholesale segment). Billing towards end-customer is Carrier’s responsibility.
There will not be any prebill set for that purpose.
17.3 Installation Charges
Installation charges are billed after the service has been installed at a site.
17.4 Rental Charges
Rental charges are billed in advance.
18. Colt Professional Services
Colt Professional Services is a team of highly focused experts dedicated to designing and managing solutions which support business transformation for our customers.
Our consultants are available to:
- Conduct thorough reviews of current and future communications requirements
- Design complex projects to exacting standards
- Manage project implementations
- Ensure the service is being delivered to customer expectations
Colt has expertise in four areas:
- Project Management
- Service Delivery
- Consulting Services and
- Design Services
For full details of the services available, please contact a Colt Account Executive.
19. Service Availability
Colt is authorized to provide telecommunications services in 31 Colt countries around the world. The Colt Country and Regions are shown in the table below.
| Northern Europe | Denmark, Finland, Norway, Sweden |
| Eastern Europe | Bulgaria, Croatia, Czech Republic, Hungary, Poland, Romania, Slovakia, Serbia |
| Western Europe | Austria, Belgium, France; Germany, Ireland, Luxembourg, Netherlands, Switzerland, United Kingdom |
| Southern Europe | Italy, Portugal, Spain |
| Asia | Japan, Hong Kong, Singapore |
| America | USA, Canada |
| Australia | Australia |
Service in Non-Colt countries
Colt is able to provide telecommunications services in over 100+ non-Colt countries, however some conditions may apply. The full details of which services Colt is allowed to provide (including SD WAN), and in which jurisdictions, is available from your Account or Service Executive.
Service availability in China
Colt can provide SD WAN services in conjunction with licensed partners – conditions apply. Please consult with your account or service executive for further details.
In addition to compliance with all regulatory requirements, the following notes also apply to China:
- MPLS is the preferred access to be used for SD WAN overlay – Customers are strongly encouraged to use MPLS for their SD WAN overlay (site to site) traffic, as it will provide the best performance and reliability. Colt can provide MPLS access as standard for the overlay (site to site) connectivity in China.
- Internet Access – may be used for VPN connectivity for site to site traffic, however this may be subject to disruption and higher latency. Customers are recommended to use MPLS only or a hybrid of Internet and MPLS access for the overlay (site-to-site) connectivity. This will provide the best balance of performance, reliability, and cost. Customers should be aware that using internet access for VPN connectivity may result in lower performance and reliability.
- Access to the Internet – Local Internet Breakout is supported at sites in china, subject to prior approval and in conformance with local laws.
Customer provided Internet will be supported.
Connectivity to Central Internet Breakout outside China is not possible. This is due to regulatory restrictions in China. Customers who need to connect to the internet from their sites in China will need to use a local internet breakout.
20. Appendix
20.1 Colt SD WAN Network Architecture
SD WAN architecture consists of following components:
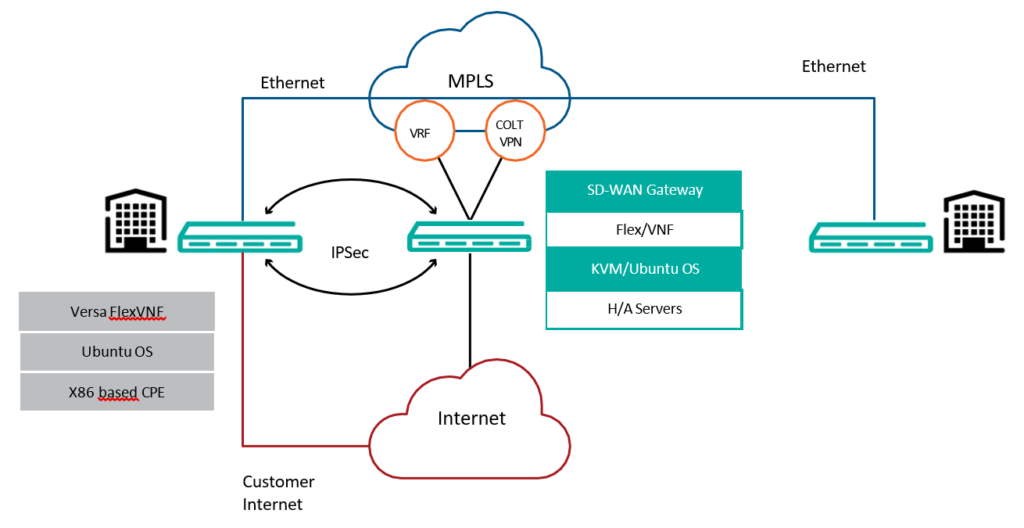
Versa Director:
This is Virtual Networks Function (VNF) manager that manages a set of FlexVNF software instances running on general purpose servers. Versa Director provides a single pane for provisioning, configuration, and management of FlexVNFs. The Versa Director will also perform the functionality of a Staging Server. A Staging Server is a registration and staging entity for deployment of all Branch FlexVNFs.
Versa Analytics (only available for Enterprise segment, in roadmap for Wholesale):
Versa Analytics is a big data solution that analyses logs, events, and provides reports, analytics as well as feedback loop capabilities. FlexVNF at various Branch-sites continuously provides monitoring data relating to link, network-path and services to the Versa Analytics server. This data can be used for dynamic application based traffic steering, capacity planning, and security forensics.
For SD WAN, the Versa Analytics supports historical and real time data reporting for:
- Application usage based on total sessions, volume, bandwidth
- Application performance based on latency, jitter, packet loss
- Performance of various paths between any two Branches
- Utilization of the different access circuit of Branches
Versa SD WAN Controller:
The Versa SD WAN Controller plays a key role in the solution and serves as a primary attachment point to the Virtual Private Network (VPN). The SD WAN Controller provides a central control-plane entry point for zero- touch deployment of Branches. The Controller authenticates the Branch FlexVNF instances using PKI certificates as part of an IKE exchange. The secure channel established using IKE provides a transport channel between a Branch node and the SD WAN Controller for transport of routes, policy, and configuration. A single SD WAN Controller can serve as the attachment point for VPNs belonging to several different customers.
Once a secure IP Sec tunnel is established it establishes MP-iBGP session with the branch CPE’s over the IP Sec tunnel.
The Controller will act as a route reflector and reflect routes between branches between each customer sites.
VNF Gateway:
The VNF gateway is used when the SD WAN sites need to communicate to Colt MPLS Sites for Hybrid solutions. VNF gateway is capable of hosting Multi Tenancy which is an important feature as a part of the solution. The VNF gateway will connect to Colt PE router as Type A NNI circuit. FlexVNFs as a service appliance at VNF gateway node, will be provisioned as virtual machines on KVM or on x86 CPE’s running any Ubuntu OS.
Versa FlexVNF CPE:
On the customer site, the Versa FlexVNFs will be deployed on bare-metal x86 servers, running Ubuntu OS.
A Branch FlexVNF can be used for providing intelligent secure connectivity (e.g. secured connectivity, Support for multiple tenants and multiple
VRFs, Intelligent load-sharing of traffic over various access circuits, SLA monitoring of multiple paths between various Branches of Routing Protocols (BGP/OSPF), VRRP, Static, QoS and CGNAT).
A Versa FlexVNF can be deployed in either of the below high availability (HA) modes:
- Inter-VNF redundancy or
- Intra-VNF redundancy
Note: Only those features, which are mentioned in the feature section of this document, can be offered to customers.
20.2 Colt SD WAN Portal Overview
The Colt SD WAN platform (available at the following URL: https://SD-WAN. colt.net/) allows Customers to check all the services that have been request- ed, and the status of each of these services. Customers can use the portal to edit traffic forwarding (over MPLS and/or Internet), set forwarding thresholds, view and edit firewall policies and see firewall, interface, DDOS and application analytics.
The portal is being continuously improved under Colt’s agile programme and will be updated without notification, customer functionalities won’t be impacted by these changes.
Please note that the portal only supports modern browsers such as Chrome, Firefox and Edge, but not legacy browsers such as Microsoft Internet Explorer.
Although the portal is a standalone web service, it uses the same authentication credentials as Colt Online; therefore, to access the portal you will need a Colt Online user account with a valid SD WAN role assigned.
In case of SD WAN Wholesale, it provides two layers of capability as shown below.
- SDWAN Reseller
- SDWAN End Customer
These two capabilities come with their own self-management portals to allow the administration of the service including for resellers and their end customers. The reseller portal view provides all the same functions as to the end customer portal but allows the end user to manage the addition and deletion Portal users from their end customers.
The capabilities of the reseller and the end user are shown will be detailed in the sections below. This guide can be split into four parts: general Informa- tion, key information, the reseller and end user guides. The key differences are that the Reseller Portal is Colt branded but the end user portal can have some splash screen and logo added to the page views for reseller branding.
As the Portal is in constant evolution, for updated and detailed information please consult the Portal User Guide available in the intranet (links below, for both Enterprise and Wholesale views)
20.2.1 Portal Specifics for SD WAN Wholesale
Please consult 4.2 section for Wholesale specifics, together with SD WAN Portal Guide Wholesale.
21. References to External Documents
References and links to other documents mentioned throughout the ESG:
Secure Network Gateway (Zscaler)
3rd Party Internet Access and SLA Tiers Regulatory Tracker
Encryption Restrictions Worldwide DCG Internal DGC Internal Service Guide
SD WAN Portal Guide Enterprise
Versa SASE Service Description
Concerto User Guide (Link to pdf)
Concerto User Guide (Link to Versa docs)
For more information, please contact us on:
+44 (0)20 7863 5510
